Advanced Wireshark tutorial: Packet and network security analysis
This Wireshark tutorial will familiarize you with Wireshark’s advanced features, such as analyzing packets and undertaking packet level security analysis.
A follow up to our previous guide (Quick and dirty Wireshark tutorial), this advanced Wireshark tutorial will help you delve into Wireshark’s more advanced features. While the first section of this Wireshark tutorial explains how to analyze packets and get the time on a router whose IP address series is known, the second section deals with security analysis using Wireshark.
Exploring Wireshark’s packet analysis capabilities
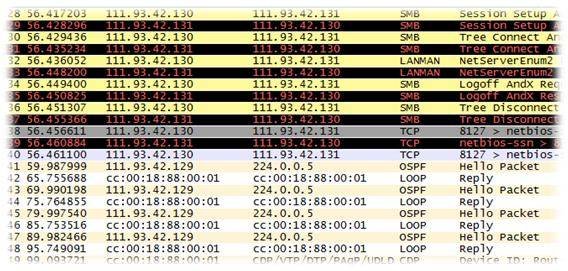
This section of Wireshark tutorial will help you analyze packets. For instance, let’s open any pcap file. Here’s how a pcap file looks in Wireshark.
Fig 1: PCAP file in Wireshark
Our first task is to find the protocol that contains time information. The dump file had Internet control message protocol (ICMP), service message block (SMB), and open shortest path first (OSPF) as the prominent protocols. The IP series of the router is 111.*.*.*
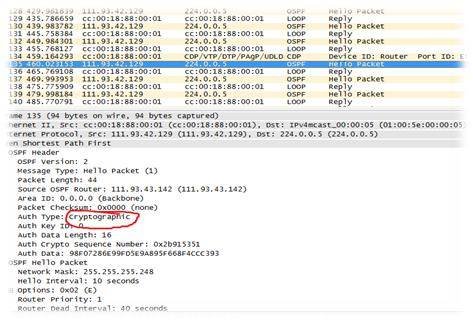
On looking through ICMP, we realize that it doesn’t contain any timestamp; SMB is also not from the router. With more information about the router having a RFC 2328 Section D.3 implementation, we conclude that the OSPF protocol contains timestamp information from the system, while Section D.3 .deals with cryptography. Thus, we start searching for cryptographic information from the packets with filter OSPF (See Quick and dirty Wireshark tutorial).
Fig 2: Cryptographic information in a packet
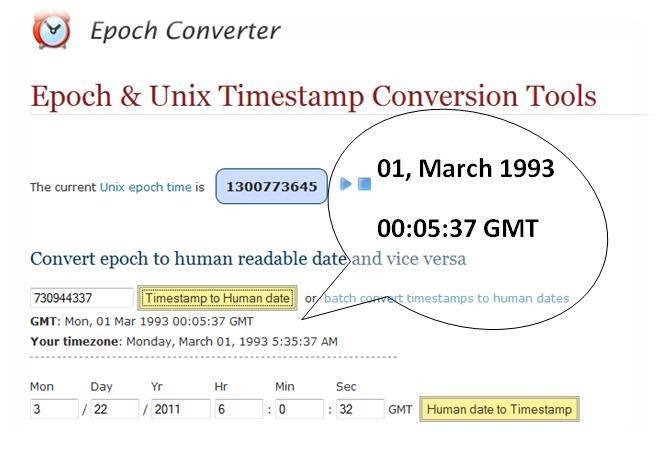
A quick conversion of the cryptographic sequence number (0x2b915351) from hex to decimal gives 730944337. Accumulating the information (in this case, a Cisco implementation) along with more data leads us to the concept of epoch time. We can use the epoch converter online tool to get the date.
Fig 3: Displaying the date and time information on the router
Security-based analysis
Now that you have mastered Wireshark’s basic concepts, you will probably be keen to explore its advanced features. This section of the Wireshark tutorial will teach you how to analyze network security at the packet level. Such analysis is important considering blackhat hacking, cyber crime, corporate data theft, and other such rising security threats.
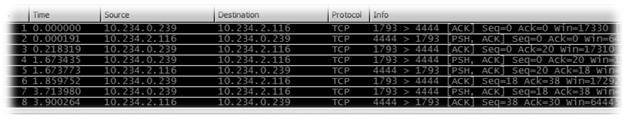
Here’s a word of caution. If you suspect that a virus or a worm has entered the system, it’s not wise to directly install packet sniffers. The malware may not let allow packet sniffers to run optimally or may completely block them. To encounter this, we can use an approach called port mirroring (the discussion of which is out of scope here). After this, capture packets from the infected system; this capture is timed in a manner such that it happens in the absence of active work. We get a capture as follows.
Fig 4: Displaying the packets captured
Checking for raw data of packets reveals more information (See Quick and dirty Wireshark tutorial). Let us look into each packet. The following screenshot does not reveal important information.
Fig 5: No important data found
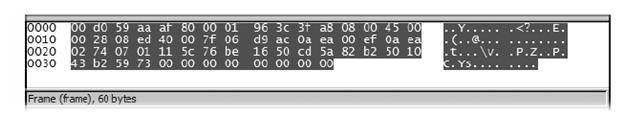
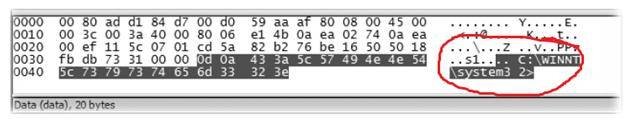
Analyzing the raw data of the following packet reveals an ongoing network communication with respect to System 32 folder of Windows. The System 32 folder houses a lot of critical data about the system in the Windows platform. We find this suspicious, as the capture has been timed with no other active work in progress.
Fig 6: Malicious access to a critical folder
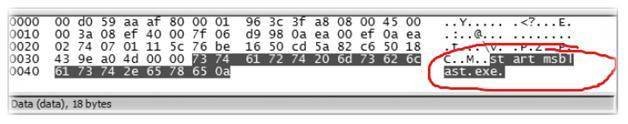
The following screenshot of the Wireshark tutorial points to a command to start the blaster worm in the target system. Thus, it’s also possible to perform a bit of forensic analysis using Wireshark.
Fig 7: Starting msblast.exe
Brush up on your Wireshark gyan quotient using our Quick and dirty Wireshark tutorial.
Reference: Chris Sanders – Practical Packet Analysis using Wireshark, No starch Press, San Francisco
Courtesy: The author wishes to thank the NULL community and Ananth Shrivastava for their guidance for the compilation of this column.
 About the author: Karthik R is a member of the NULL community. He is also the founder member of a startup named Raining Brains Security Solutions, which focuses mainly on security issues in the cyber world. Karthik completed his training for EC-council CEH in December 2010, and is at present pursuing his third year of B.Tech in Information Technology, from National Institute of Technology, Surathkal. Karthik can be contacted on [email protected].
About the author: Karthik R is a member of the NULL community. He is also the founder member of a startup named Raining Brains Security Solutions, which focuses mainly on security issues in the cyber world. Karthik completed his training for EC-council CEH in December 2010, and is at present pursuing his third year of B.Tech in Information Technology, from National Institute of Technology, Surathkal. Karthik can be contacted on [email protected].
You can follow our Twitter feed at @SearchSecIN