10 Linux security tools for system administrators
Linux-based tools for security are a boon to system admins for monitoring network security. Here are 10 popular and useful Linux-based security tools.
In recent times, the security aspect of information technology has received considerable attention, and large organizations have dedicated security teams to keep tabs on vulnerabilities in their systems and take preventive or corrective action as appropriate. The same level of commitment to maintaining security may not be seen in most SMBs, but the fact remains that any gaps in security could have disastrous consequences for all businesses, regardless of their size.
Security need not always be a hugely expensive affair. In this article, we shall cover Linux-based security tools and distributions, which can be used for penetration testing, forensics, reverse engineering, and so on.
Network analyzers and scanners
Network analyzers and scanners are an important category of tools in the arsenal of a system administrator to monitor the network activity of the enterprise. The most used Linux security tools in this category are as follows:
1. Wireshark:
Wireshark (formerly known as Ethereal) is a very powerful packet analyzer for system administrators. Its features include live capturing of packets; browsing the contents of the packet; and, understanding various protocols and their parts. We have already covered Wireshark in detail in an earlier tutorial.
2. NMAP:
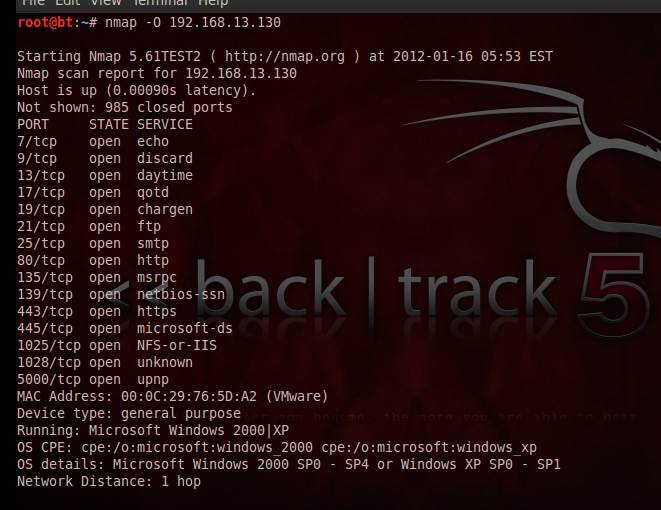
Another Linux-based tool for security is NMAP, a must-have security scanner. It analyzes raw IP packets and then provides details about the live hosts in the network along with their banner information, ports, services and versions running. Any unintentionally open port on the target system can be detected by the tool, and necessary action can be taken. There are two versions of NMAP available, a command line interface and a graphical user interface known as Zenmap. While both have essentially identical functionality, the GUI version has inbuilt scan profiles to readily scan the target.
Figure 1. NMAP in action
Figure 1 shows NMAP scanning of the target, with the ports on the system, the services running, and also the states of the ports. You can also see the banner information of the target, through the OS fingerprinting feature. Complete information on the NMAP command set can be found at: http://www.computerhope.com/unix/nmap.htm.
3. Malware, antivirus scanners
The Linux platform is seeing development of antivirus and other security enhancers to make things easy for a layman. Among Linux-based tools for security, ClamAV is an antivirus software program written exclusively for a Linux distro. It is designed to detect Trojans, viruses, malware and other threats on the system. For seeking out the rootkits in your distros, the readily available programs are chRootkit and Rootkit Hunter.
Intrusion detection tools
This category of Linux-based security tools covers tools that are widely used for intrusion detection. It is vital for administrators to have IDS tools in the kit, because an enterprise network is always susceptible to the attacks of malicious hackers intending to steal data.
4. Snort:
Among Linux-based tools for security, Snort is a very powerful free, open-source tool that helps in the detection of intruders and also highlights malicious attacks against the system. In effect, Snort is merely a packet filter. But the true value of this tool lies in its signature-based detection of attacks by analyzing packets that Wireshark or tcpdump are incapable of analyzing.
Figure 2. Snort directory
Figure 2 shows the /etc/snort directory in the Backtrack Linux distro. Here we can see the snort.conf and rules. Snort.conf is the file in which one specifies “internal network” (safe IPs) and “external network” (potentially dangerous IPs).
>>>>>>>> snort.conf>>>>>>>>
Var HOME_NET <ipaddress>
Var EXTERNAL_NET <ipaddress>
The skill of using snort lies in configuring its rules, such that legitimate traffic is permitted and illegitimate traffic is flagged.
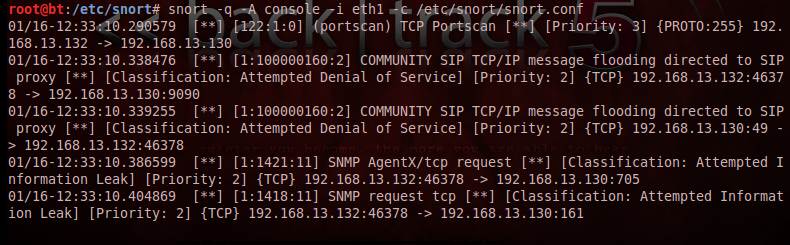
Figure 3. Snort alerts
Figure 3 shows a screenshot of snort alerts for a port scan on the target from the attacker system. Similarly, snort can be used for malicious payload alerts, or any other noise in the network, based on the analysis of the attack signatures.
5. NIKTO:
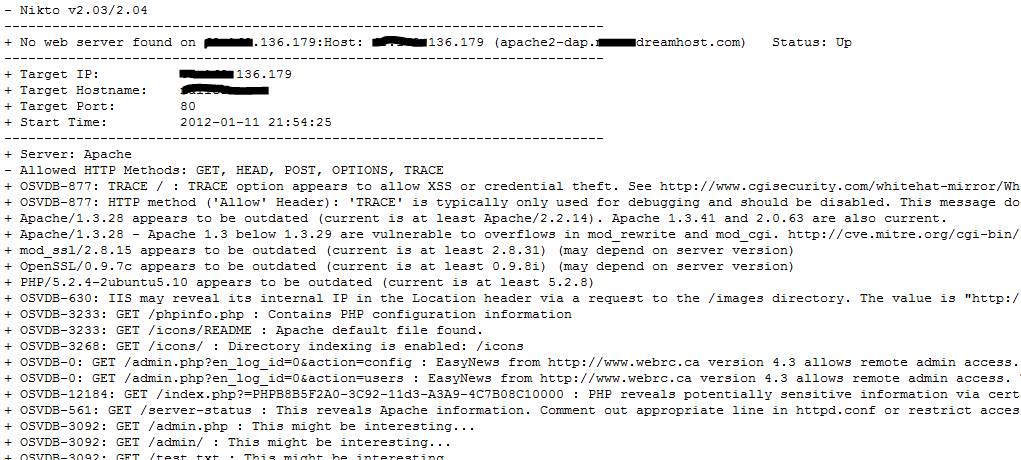
NIKTO is another open source Web server scanner that tests Web servers for potentially dangerous CGI files. It also performs version-specific analysis, such as identifying outdated frameworks. NIKTO can also be used to test IDS systems. One must note that every test or check report doesn’t necessarily point to a security problem, hence the person analyzing NIKTO reports needs to be careful in this regard. Figure 4 shows a screenshot of a NIKTO report on a Web server.
Figure 4. NIKTO report screenshot
6. Metasploit framework:
Metasploit is one of the most popular Linux-based tools for security. It started out as a networking game, but grew into an exploit development framework. Metasploit contains a large set of modules for various applications in network administration. The features of Metasploit, various attack vectors, and analysis of network traffic have been covered extensively under our Metasploit tutorial series.
Figure 5. Src folder in SPIKE
7. SPIKE:
SPIKE is a network fuzzing tool that helps in understanding various protocols. Fuzzing is necessary when testing an application for abnormal behavior such as buffer overflows and stack overflows. This is a very important stress testing tool, on the network as well as on the application.
The working of SPIKE is based on spike scripts, which have the .spk extension. The spike ‘src’ folder has many scripts that can be used for fuzzing an application/network. Figure 5 shows the src folder of SPIKE.
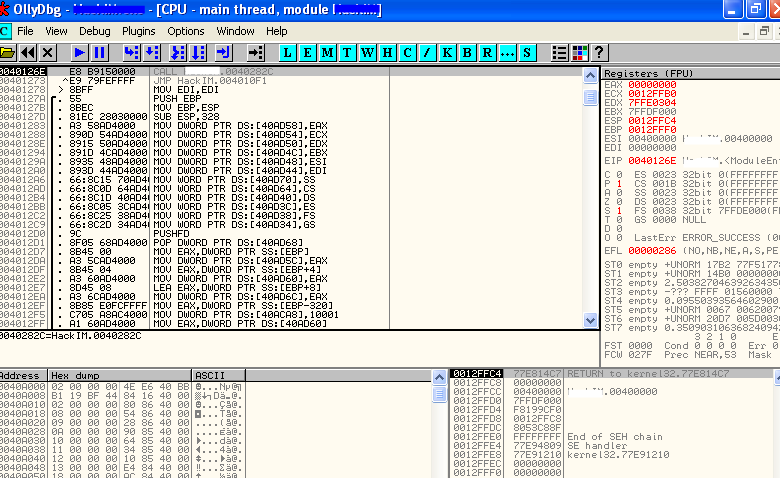
Figure 6. Ollydbg debugger
8. Ollydbg debugger:
The Ollydbg debugger is a handy utility to help understand an application by reversing it and analyzing the calls to memory and various other dlls. Even though this framework is more prominent for Windows platforms, Linux users can check it out in the Backtrack Linux distro. As mentioned above, integrating debuggers with a fuzzer such as SPIKE can be very handy during security testing.
9. Nessus vulnerability scanner:
Nessus is a Windows- as well as Linux-based automated network vulnerability and audit tool. The system monitors network traffic to expose vulnerabilities such as SQL injection, cross-site scripting, missing patches in the system, vulnerable servers, and so on. The framework works by running a Nessus server that constantly updates itself for the latest plug-ins. While this Linux-based security tool needs to be purchased for commercial use, home users can download it for free.
10. Linux-based security distros:
There are various security distributions of Linux available on the Internet. These security distros have pre-installed tools and frameworks for monitoring traffic, carrying out penetration testing, and other security related analysis. Here are a few notable ones:
- Backtrack Linux – A very popular pen-testing distro.
- Matriux – An Indian version of Backtrack, with pen-testing tools pre-installed.
- Remnux – A Linux distro mainly used for executing forensic applications.
 About the author: Karthik R is a member of the NULL community. Karthik completed his training for EC-council CEH in December 2010, and is at present pursuing his final year of B.Tech in Information Technology, from National Institute of Technology, Surathkal. Karthik can be contacted on [email protected]. He blogs at http://www.epsilonlambda.wordpress.co.
About the author: Karthik R is a member of the NULL community. Karthik completed his training for EC-council CEH in December 2010, and is at present pursuing his final year of B.Tech in Information Technology, from National Institute of Technology, Surathkal. Karthik can be contacted on [email protected]. He blogs at http://www.epsilonlambda.wordpress.co.
You can subscribe to our twitter feed at @SearchSecIN