Five DDoS attack tools that you should know about
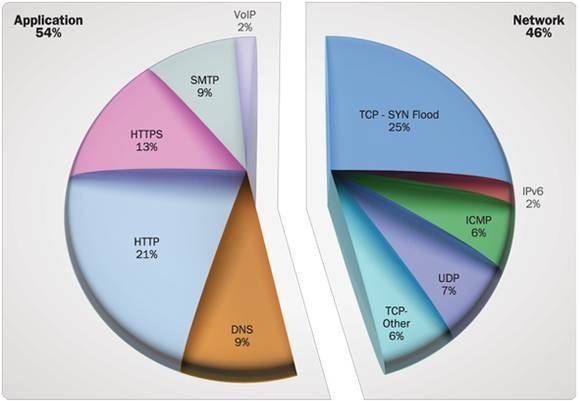
2011 saw a surge of DDoS attacks, surpassing all previous records. Surprisingly a majority of these distributed denial-of-service attacks were not attributed to bandwidth constraints. In the accompanying graph it is clearly seen that network-based DoS attacks were less than application-level DDoS attacks. A majority of the attacks exploited the HTTP and its sibling HTTPS protocols. Attackers realize that volumetric attacks can be mitigated by use of scrubbers on the cloud, so they opt for slow and low DoS attacks, choosing applications as the target instead of networks.