11 security audit essentials
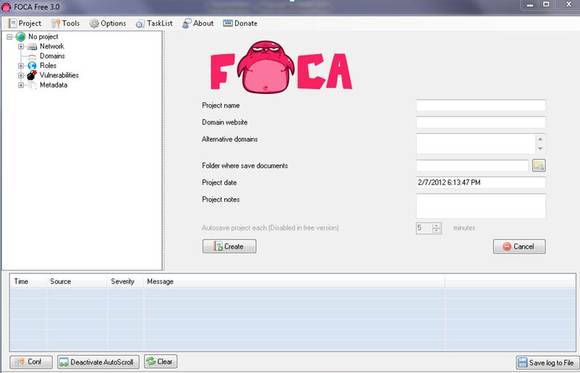
Our second recommendation for IT security audit tools is the reconnaissance-based framework known as FOCA. This network infrastructure mapping tool can extract extremely sensitive information from the target. FOCA analyzes metadata from various file formats, including Microsoft Word and PDF files. It can also enumerate files, folders, software used to create the file, and also the operating systems. Small wonder then that one often hears the phrase, “Fear the FOCA!”
You can download this tool here.