Sandboxing for secure app development: Adobe Reader’s 'protected view'
Adobe Reader’s whitelisted actions
- Writing to the user’s TEMP folder
- Writing (saving) Adobe Reader-specific user-modified preferences to the registry
- Launching a helper process called the tracker to handle shared reviews for PDF documents
- Launch non-PDF attachments from within the PDF file in their native application
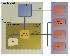
Adobe Reader X uses a dual-process architecture make up for functionality lost through sandboxing. A broker/user- rights process that runs alongside the sandboxed process ensures indirect and secure policies-based access to objects, assisting whitelisting operations that sandboxed applications may perform. Policies are programmatic interfaces that allow the broker processes’ APIs to define restrictions. The broker process communicates with the sandboxed process through a secured inter-process communication (IPC) gateway using a shared memory and event mechanism.
Reader’s sandbox has two distinct security principals: the user principal, or the user’s logon session, and the PDF principal (the isolated process that parses and renders a PDF). This distinction is established based on a trust boundary at the process level between the sandbox process, rest of the user’s logon session, and the operating system.
>>Go back to the main article<<