Sandboxing for secure app development: Adobe Reader’s 'protected view'
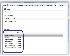
Generation of process tokens in Adobe Reader’s sandbox
- Deny all SIDs except: BUILTIN\Users, Everyone, User’s Logon SID, NTAUTHORITY\INTERACTIVE
- Add the following Restricting SIDS: BUILTIN\Users, Everyone, User’s Logon SID, NTAUTHORITY\RESTRICTED
- Adding a low integrity level SID (only for Vista, Windows 7, and Windows Server 2008)
- Removing privileges. All privileges except the SetChangeNotifyPrivilege are removed from target process access tokens.
Access tokens are objects that describe a process’s security context (identity and privileges of the user account associated with that process) in a sandbox. Adobe Reader uses restricted user access tokens to restrict the read, write and execute capability of processes. A restricted access token is a modified token (using the CreateRestrictedToken function), which is effective in limiting access to any objects protected by a discretionary access control list (DACL).
Restricted tokens in Reader’s sandbox are created by modifying the two token components — denying/restricting the Secure Identifiers (SID) and dropping off privileges. The resulting token effectively allows writing to only those locations (in file system or registry) that USERS or EVERYONE has access to – effectively ruling out the entire user profile directory (My Documents, Startup, Temp, etc) and the system directory (C:\Windows*).
>>Go back to the main article<<