
gluke - Fotolia
Three things you may not know that DNS data can tell you
Big data tools can help network administrators gather new insights into security and performance from DNS data
If you're a network manager, you'll be familiar with the domain name system (DNS). For the uninitiated, it's essentially the internet's equivalent of a telephone directory, storing the names of computers and their IP addresses.
DNS queries are generated every time someone visits a website or sends an email, translating the domain name into an IP address to find the correct computer.
Network managers can use DNS data to understand what's happening on their networks. However, the sheer volume of data can make that job a significant challenge, especially when you consider all the other log files and security data network managers need to review.
In large organisations with big networks, it's not unusual to have multiple domain name servers running, making the task that much harder. While tools exist to give you visibility of the data, deciphering meaningful signals or insights from a vast number of data points isn't easy.
Historically, there haven't been any tools to help analyse DNS data in-depth and in real time. But now, sophisticated big data techniques have enabled us to create a tool that can analyse terabytes of DNS data in real time.
As a result, a new world of intelligence and insights from the DNS can be gleaned.
Detailed below are three interesting things that Nominet, sitting at the heart of the ".uk" internet infrastructure, has observed in the months we've been testing and developing this technology:
Detect spam runs and botnets
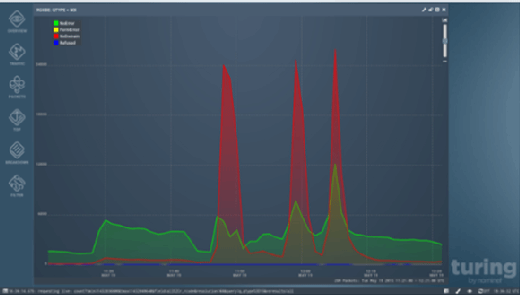
During a spam run, huge numbers of emails are sent out to a pre-defined, and often outdated, list of addresses. As a result, requests for domains that no longer exist are very high.
In the above graph, unresolved DNS queries are represented by the red spikes. This sort of pattern recognition can also help you recognise botnet infections on your network, allowing network administrators to identify and deal with compromised machines, ultimately tackling a key source of spam and malware closer to its source.
Network optimisation possibilities

DNS data can reveal anomalies in traffic hitting your network, and can be used to identify the cause of network latency that could result in delays in transmission and processing, and therefore in the quality of service network users' experience.
The illustration above is an unfiltered view of the DNS, with the colours representing the "health" of the traffic. Further investigation may lead you to restructure the way your DNS servers are configured and potentially reduce latency on key applications -- or indeed reduce bandwidth costs.
Software vulnerabilities
There is a pattern and consistency to healthy DNS traffic. When certain events occur, for example a disproportionate number or unusual pattern of Servfail responses, it may be an anomaly -- or it may indicate a software vulnerability. It could also illustrate poor configuration of a server that might expose you to unnecessary risk. We discovered problems with Google's Public DNS and a hidden bug in Bind, the widely used DNS software, by deploying these techniques -- both have since been resolved.
DNS analysis has historically been a challenge to analyse meaningfully, so it has rarely played a sophisticated part in organisations' cyber defence or network optimisation strategies.
But given these new insights we can tap into -- whether battling distributed denial of service (DDoS) attacks, fixing vulnerabilities and addressing latency in the network or shutting down spam -- DNS no longer has to be an unknown quantity, and can be used to your advantage.
 Simon McCalla is chief technology officer at Nominet.
Simon McCalla is chief technology officer at Nominet.









