
Maksim Kabakou - Fotolia
Security Think-Tank: Tackle insider threats to achieve data-centric security
The belief that effective perimeter security is the best way to protect data is a fallacy that is being repeatedly exposed. We must recognise the need for a data-centric security model to protect data from both internal and external threats, but what does this mean for security professionals?
Perimeter-centric controls are vital for stopping adversarial (and sometimes also accidental) threat actors. However, they have little to no effect against insiders and become all but useless once a breach occurs.
To optimise security arrangements, organisations should adopt a data-centric security model that makes use of preventative, detective and reactive controls, putting in place measures that assume breaches will happen so as to create organisational resilience.
Insiders are involved in the majority of security incidents. This can be with malicious intent (such as stealing data from the organisation), by accident (misconfiguring a system, for example) or through negligence or inadvertent error (such as falling victim to phishing – the most common vulnerability).
As insiders are able to bypass many controls, perimeter-based solutions are not adequate to protect an organisation. Additional measures are required for each stage of the information lifecycle to ensure data is protected as it is copied, shared, reused, repurposed, backed up or archived.
Variations of the information lifecycle exist. The ISF uses the following information lifecycle:
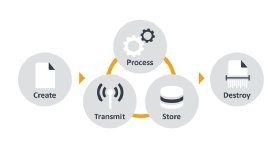
Throughout this lifecycle, insiders have access to their organisation’s information. If organisations are going to protect their data better and reduce the frequency and impact of incidents, security controls must take account of the insider threat.
Information risk assessments will determine the appropriate controls for the specific threat events associated with each stage of the lifecycle that take advantage of the trust vested in insiders. As a minimum, basic cyber hygiene measures are vital. These include access control, segregation of networks, anti-malware solutions and patch implementation.
But security controls can, and do, fail. More than 90% of incidents are caused by control failure, suggesting controls alone are insufficient. Incident response, recovery and governance functions all form part of the required solution in the following manner:
- Responders minimise the potential impact of security incidents – applying the necessary measures to isolate and treat affected endpoints, engage with pertinent stakeholders and coordinate required expertise, such as forensic technicians.
- Recovery teams work to restore information systems from backups and bring productivity back to where it was before the incident occurred.
- Governance bodies, such as a steering committee, facilitate the planning, resourcing and overall provision of these and other services (before, during and after an incident). They should also be responsible for evaluating the findings from post-incident analysis and putting in place suitable remediations to prevent the incident from reoccurring.
These functions need to prepare and practise for incidents, because it is stressful and challenging to operate in a time-pressured, adrenaline-fuelled moment of chaos. A range of options, such as table-top exercises, red/blue (purple) teaming and war rooming, can help to develop the requisite skills in advance of a major incident.
Performing these functions relies on a frame of mind and skillset that typically differs from the conventional security practitioner. In many ways, an incident response capability is akin to the emergency services, while the latter role can be likened to a builder. Both skillsets are vital, but can rarely be performed by the same individual.
Organisations therefore need to recruit individuals with varied skills, aptitude and attitude (either internally or via a third-party provider) to ensure they can effectively secure enterprise data as part of a resilient data-centric security model. This will help to reduce the probability of becoming one of the 61% (and rising) of those reporting a cyber security incident to insurers in 2019.








