
plus69free - Fotolia
Changing the rules against cyber attacks
UKRI’s John Goodacre reveals how projects supported by the Digital Security by Design Challenge aim to improve cyber security resilience, beginning with the very fundamentals of computing
Today, cyber security is a continuous escalation of attacks against a defence of keeping up with your software patching and attack monitoring. Zero-day vulnerabilities cause significant effort and cost when those at risk rush to protect themselves.
For decades, computers have been vulnerable due to design errors and bugs in software, resulting in data breaches and their operation being held to ransom. The world of cyber security has evolved around knowing if you are being attacked, and managing the risks and opportunities of been attacked, as opposed to blocking or removing any fundamental issues in a computer’s design.
This poses two fundamental questions – why is the only solution to keep patching, and why hasn’t a way been found to block the consequences of a vulnerability? In short, why do we only treat the disease, rather than manage the illness?
One answer could be that the fundamental architectural design of the way a computer’s processor executes software has remained the same. This is because unless a new chip has software to run, it won’t be built. Likewise, those that write software will target the chips that are already built. This is a clear catch-22 that has meant any changes seen so far in a processor architecture are “in addition” or “around” the fundamental approach to how it works.
At UK Research and Innovation (UKRI), we want to bring about a fundamental shift in the way we ensure computers are protected from cyber attacks. UKRI’s Digital Security by Design Challenge (DSbD) was created to deliver technologies that can bring a whole new rule book in which cyber vulnerabilities would be blocked by design and protect by default the computer’s operation and data.
Improving memory safety has been a target of various new approaches in software. These have typically either excessively degraded performance, overly constrained the software or required the ground-up rewrite of billions of lines of code. Also, all these proposals are still just software, which further increases the possibility of introducing additional vulnerabilities.
Formal software verification and advanced testing methodologies are also being used more. However, without having a formal specification for the hardware, such verification is only as good as its assumptions on how a computer works. The increasing rate of reported vulnerabilities shows that the overall situation is getting worse, not better, as more software is written and reused in new ways.
The Morello programme
The CHERI research programme at the University of Cambridge had investigated what fundamental, but incrementally deployable, changes could be made to the architectural design of a processor so that the hardware itself can implement a memory-safe design while not overly constraining typical software design practices.
The first project UKRI funded was with an Arm-led consortium, in which their Morello programme is investigating how the CHERI concepts can be applied to a mainstream processor design.
Unlike in existing processors, in which a software program or the operating system can manipulate large regions of a computer’s memory, the CHERI design principle is to ensure access is limited to the fine-grain regions of memory that the software intended it could access.
This would mean a cyber attack that would have typically injected new code through a computer vulnerability simply cannot happen because the vulnerable code, by design, does not have the permission to do that.
One of the main outcomes of the Morello programme is a development board that can be used by software developers to investigate the new processor design.
Compartmentalisation
In addition to offering memory safety, the CHERI researchers also proposed a mechanism to offer software the ability to place its code, its libraries, and its data into compartments. Compartments offer a fine-grain mechanism to isolate different parts of a program design, which again has hardware-enforced hierarchy of privilege asserted to stop other parts of the software gaining access, whether that software is part of the same code, or has found its way maliciously into the machine.
While software sandboxing is used today in a coarse-grained way, CHERI compartments provide a fine-grained mechanism. It could mean that, for example, every image or code block in your web browser, every message attachment you view, or the keystrokes you type as you enter a password, can be all isolated in their own sandbox. This is impossible to do with today’s hardware.
Arm has previously shared the below image to show how malicious code can be contained within one compartment, rather than gaining access to the entire content.
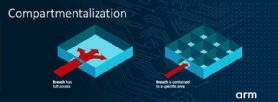
It should be clear that the DSbD technologies are not a silver bullet that will kill all vulnerabilities on day zero. Firstly, the computer will need to be using one of the newer processor chips that includes the DSbD technology features.
The operating system will need to “turn the features on” and, as a minimum, will be able to better isolate the various components under its management. Software applications will, over time, then need to be compiled to enable the memory safety features, with software needing to be structured to benefit from compartmentalisation.
Developing new chips
The DSbD programme is working to encourage that all new chips will, in time, be able to support these new features. Working with Arm should mean billions of new chips will become available over time. With the support of various operating system companies, including Microsoft and Google, the products and services using these devices will have an increased resilience against cyber attacks without needing to change the applications, but users will need to be using the new hardware.
When applications start to be compiled as memory-safety aware, we will start to see the continuous flow of high-impact vulnerability reducing, with the cost and lost productivity of zero-day attacks lowering significantly. When the software developers then start to compartmentalise software, we should see a further reduction in the consequence of a much broader class of cyber attacks.
The DSbD programme is supporting the creation of this full ecosystem and value chain, working to reduce the time, barriers, complexity and risk of adoption.
Securing the future
With the way we all experience digital exposure of personal data, seeing businesses being held to ransom, and with critical infrastructure becoming a state weapon, can we really believe that tomorrow’s AI won’t also be hacked and its ability to function not compromised – streets full of cars going crazy, the lights going out or all your communications getting corrupted or exposed?
It is not impossible to see a digital future in which people and businesses shy away from the digital world, delete their online presence, maintain mechanical manufacturing, and refuse to access online services.
DSbD is working to ensure a bright digital future. The resilience, safety and security of everything in the digital world must be considered and how they can become secured by design and be protected by default.
DSbD’s work with the key businesses and researchers will create the infrastructure on which these new product and service developers can use to answer this challenge. Let’s make sure everyone demands that they do – for their benefit, and for ours.
John Goodacre is professor of computer architectures at the University of Manchester and is director of UKRI’s Digital Security by Design Challenge








