
cherezoff - stock.adobe.com
Killnet DDoS hacktivists target Royal Family and others
Russia-aligned hacktivists targeted multiple UK websites, including those of the Royal Family, in a new campaign of DDoS attacks
The Killnet collective, a group of hacktivists aligned with the Russian state’s interests, claim to have caused significant disruption to multiple websites and organisations in the UK in a wave of distributed denial of service (DDoS) cyber attacks, supposedly in revenge for the government’s support for Ukraine.
A DDoS attack is a relatively crude form of cyber attack in which multiple compromised systems or botnets flood their targets’ server, website or network resources with messages, connection requests or malformed packets, causing them to slow down or crash. They tend to be deployed mainly to cause disruption rather than for financial gain, although recently some DDoS attacks have been accompanied by extortion demands.
In messages posted to the Telegram messaging service seen by Computer Weekly, Killnet members said they had attacked the Bankers Automated Clearing Service (BACS), the London Stock Exchange, and the official website of the Prince of Wales.
In one message, Killnet said that the “royal official site” was not working. “Perhaps this is due to the supply of high-precision missiles to Ukraine,” the group said.
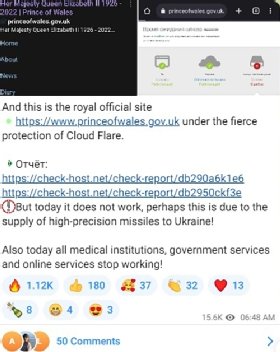
“Also today all medical institutions, government services and online services stop working,” they added.
At the time of writing, all three of the abovenamed websites were operating normally, although the Prince of Wales’s site – which has not yet been updated to reflect the new bearer of the title, Prince William – has implemented additional security checks for incoming web traffic.
The Killnet group has risen to prominence in recent months, targeting organisations around the world in countries opposed to Russia’s attack on Ukraine. Recent high-profile targets include the US Department of the Treasury and the FBI.
Although its methods are unsophisticated and its attacks have caused limited disruption, it has become one of the more active cyber mercenary groups to have emerged from the Ukraine war, and is easily the most prominent manifestation of cyber warfare beyond the theatre of conflict.
It is known for staging “aggressive and rhetorical” misinformation campaigns on its Telegram channel, which has almost 100,000 subscribers, and enjoys publicly mocking its victims.
“Killnet is a prolific political pro-Russian hacking group that moves targets every few weeks based on geopolitical developments,” said Muhammad Yahya Patel, a security evangelist at Check Point.
“As a major player in the hacktivism space, they also suggest and define the targets for other pro-Russian groups. We have seen a 42% global increase in cyber attacks since the start of the Russia-Ukraine war, with a significant rise in state-sponsored groups.”
Patel added: “The affected websites were back up and running quickly after the attack, which is a good sign that they have appropriate measures in place. The best advice to all is to remain vigilant and prioritise preventative security on all endpoints. Make sure you have the right levels of protection and monitoring against DDoS attacks. Have a robust data backup solution that isn’t connected to the same network.
“Always use up-to-date software and security patches, prevent email attachments and files being downloaded without scanning the contents first, and provide comprehensive cyber awareness training for every employee. By taking these steps, you can reduce risk and remain secure against highly organised cyber crime gangs.”
Read more about Ukraine-linked DDoS attacks
- A quarter of cyber security incidents reported to the Financial Conduct Authority in the first six months of 2022 involved DDoS, with a likely link to events in Ukraine.
- There has been a boom in distributed denial-of-service attacks in the first six months of 2022, according to a report, with Russia’s war on Ukraine helping to drive activity.








