
peterschreiber.media - stock.ado
Ukraine cyber attacks seen spiking, but no destructive cyber war yet
While cyber attacks linked to Russia’s war on Ukraine are taking place, they are having little impact beyond the region
As the war in Ukraine continues, large-scale, targeted Russian cyber attacks against targets in Western countries have failed to materialise, as far as we know, but observers are nevertheless reporting significant spikes in malicious cyber activity, albeit without sustained or damaging impact.
Data released this morning (Monday 28 February) by Check Point Research shows a 196% increase in cyber attacks on Ukraine’s government and military sector. Worldwide, government and military bodies showed no similar increase.
“Cyber activity is surging around the ongoing Russia-Ukraine conflict,” said Check Point’s head of threat intel, Lotem Finkelstein. “We’re seeing cyber attack increases on both sides, with the Ukrainian government and military sector seeing the heaviest increase.”
Check Point also observed a notable 4% increase in attacks directed at Russian organisations more generally, compared with a 0.2% increase in attacks directed at Ukrainian organisations. Globally, other regions have experienced net decreases in attack volumes.
With Ukraine lacking much of a capacity to conduct open cyber warfare – although Kyiv is seeking assistance in this regard – this surge in activity targeting systems located in Russia is generally considered to be the work of hacktivists, among them people associated with the Anonymous collective.
Since Anonymous appeared to declare war against the Russian government last week, targets have included TV stations, some of which were reportedly hacked to play the Ukrainian national anthem, and government departments. Most of these attacks appear to have been distributed denial of service (DDoS) attacks.
Finkelstein said: “People online are choosing sides, from the dark web to social media. Hacktivists, cyber criminals, white hat researchers and even technology companies are picking a clear side, emboldened to act on behalf of their choices.”
It is important to remember that playing an active role in the execution of a DDoS attack as a civilian hacktivist is illegal, even if it is against a hostile nation state. Anyone taking part in these actions may be at risk of prosecution and risks collateral damage to important IT systems and network infrastructure in non-combatant countries.
Significantly, Check Point analysts also reported that volumes of phishing emails in East Slavic languages have increased sevenfold, with one-third of these originating from within Ukraine and targeting recipients in Russia.
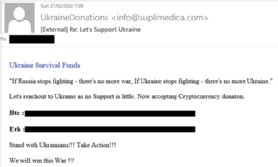
However, given the outpouring of global support for Ukraine as it faces down an unprovoked attack from a nuclear-armed dictator, Check Point has unsurprisingly also seen a surge in fraudulent emails attempting to dupe people who want to donate to the Ukrainian cause from abroad.
IT and security teams should take steps to encourage their users to spot and ignore phishes linked to the war on Ukraine by paying attention to misspellings in email addresses and domains. For example, lower-case Ls can appear similar to upper-case Is or even the number one in some font sets, and vice versa, or the letters R and N in lower case can masquerade as Ms.
Malicious actors may also be writing in a language that is not their own, so users should also pay attention to spelling and grammar within the email. Notably, native speakers of Russian and Ukrainian often misuse, or forget to use, the definite article when writing or speaking in English.
Also, attached files may be used to spread malware or ransomware, so be hyper-vigilant if receiving unexpected attachments from outside sources.
Given the emotive circumstances, cyber criminals are also likely to attempt to use psychological tricks to create a sense of panic or urgency.
“For people seeking to donate to Ukraine, we are issuing strong caution of fraudulent emails seeking to capitalise on your willingness to give,” said Finkelstein. “Always check the email address of the email sender. Watch for any misspellings in emails. And verify if the email sender is authentic. We’ll continue to monitor all sides of the cyber activity around the ongoing war.”
Read more about cyber warfare in Ukraine
- A wave of DDoS attacks, and a second data wiper attack, were seen hitting Ukraine in the hours leading up to the Russian invasion.
- Intelligence officials say they have no evidence or indication that Russian cyber attackers are preparing offensive assaults on infrastructure or organisations in Britain.
- A series of DDoS attacks on Ukrainian defence and banking organisations last week is now being firmly attributed to Russian action.







