REvil affiliates offer hefty ransom discounts, data reveals
REvil or Sodinokibi ransomware activity is higher than ever, but its success appears to be relative, with some affiliates prepared to dramatically cut their prices
The REvil, or Sodinokibi, ransomware crew and its affiliates appear to have aggressively ramped up their attacks in June 2021, according to data obtained by LeMagIT, Computer Weekly’s French sister title.
LeMagIT found 35 total victims in the past 30 days, slightly more than in April, which is up 30% over the franchise’s most active periods, namely August and October of 2020, and February and March of 2021.
The number of pages on the crew’s dark web leak site gives an indication of the extent of the syndicate’s activity: it listed 356 victims as of 3 June 2021, and 383 as of 28 June, for a total of 27 new victims during the period. Eight seem to be missing, which may indicate they have paid a ransom, although the reality may be different.
Of the REvil/Sodinokibi samples collected during June, five appear to highlight negotiations that led to at least partial payment of a ransom, a success rate of around 20%. This is ‘better’ than the group’s affiliates achieved in April and May, but appears to have come at a cost – in the form of deep discounting.
In the first case analysed by LeMagIT, the initial ransom demand was for $500,000 but the payment made was just under $281,000. In a second incident, the negotiations opened at $50,000 but a deal was quickly reached for a ransom of $25,750. The third case is probably the most spectacular, with the cyber criminals making an initial demand of $300,000 but settling for only $50,000 – payment occurred four days after the start of the discussion.
The same phenomenon was observed in two other cases. The first resulted in a ransom payment of $17,467 instead of the $100,000 originally requested, following discussions that lasted almost a month. In the second case, the mobsters were satisfied with $15,300, after three weeks of negotiations, having demanded $90,000 to begin with.
These sums do appear to be somewhat low compared to other high-profile ransoms paid in recent months, but the victims also seem more inclined to resist – LeMagIT observed one negotiation initiated on the basis of a request for $2.5m, but the victim rapidly terminated discussions.
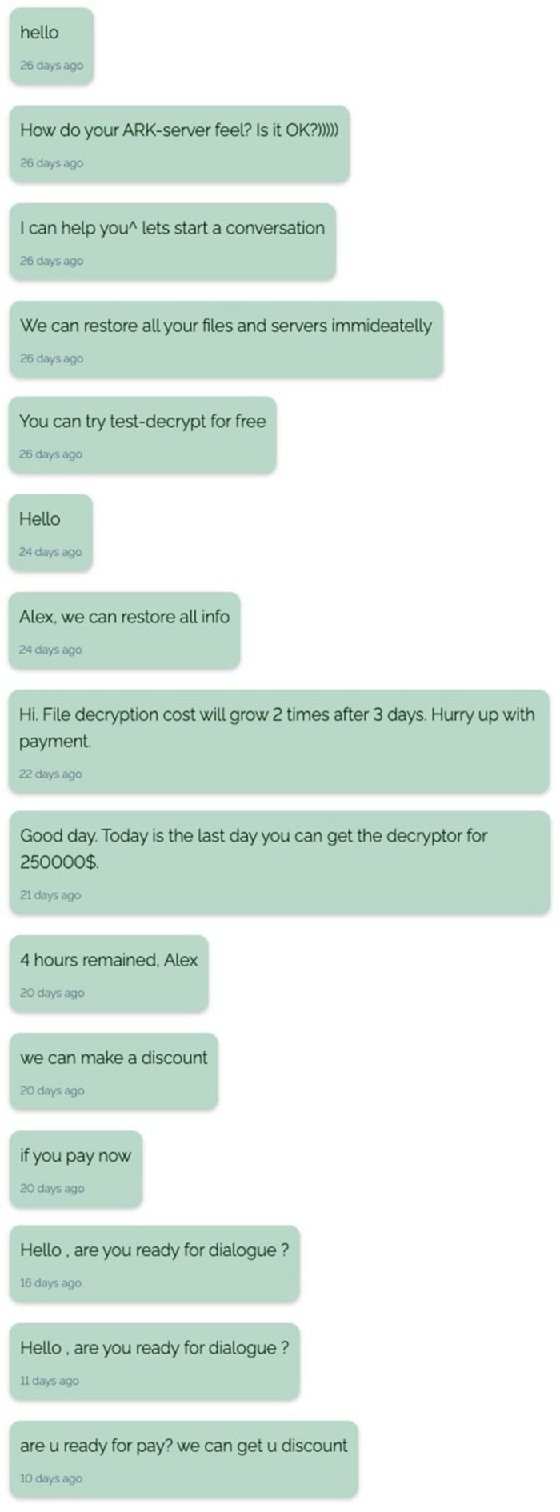
When asked at the start of June about its activity by a Russian-speaking threat intelligence specialist, a REvil representative nevertheless claimed the group was doing well, and said that demand for access to the gang’s ransomware-as-a-service (RaaS) programme was high, with eight candidates applying for a single spot.
The REvil crew is also apparently still investing in its RaaS platform, with the Linux version of its encryption tool – first announced in April and available since early May – now observed in the wild for the first time. This tool begins its work by shutting down all virtual machines (VMs) on the ESXi host on which it is deployed before then engaging encryption, as observed by Vitali Kremez of Advanced Intelligence.
But the gang could also have some links to other groups, possibly even several. Recent investigations by the SecureWorks team have found that the emergent LV ransomware is heavily based on Sodinokibi code – however, they do not address questions that may arise from the existence of two different leak sites for LV’s extortion operations, one of which has recently become unavailable, possibly temporarily.
Nor do these elements shed any light on the mystery that hangs over another ransomware campaign, known as Lorenz.sZ40 (apparently named for one of the Nazi cipher machines cracked at Bletchley Park during World War II). Though researchers at Intezer do not see any link in the binary code with REvil/Sodinokibi, the web interface for making ransom payments is nothing more than a copy of REvil’s, albeit lacking a live chat module.
Read more about ransomware
- RUSI think tank calls for an industry-wide reset amid intense challenges for providers of cyber security insurance as ransomware challenges mount.
- Report produced for MSSP Talion claims overwhelming support for the criminalisation of ransomware payments.









