
Funtap - stock.adobe.com
FBI planned a sting against An0m cryptophone users over drinks with Australian investigators
Australian Federal Police and the FBI came up with the idea over drinks: build a cryptophone network with a built-in backdoor and sell it to crime gangs around the world
Three years ago, the FBI began planning a sophisticated sting that led to the arrests of 800 suspected organised criminals in raids around the world.
Police this week carried out hundreds of searches, seized drugs, firearms, luxury vehicles and cash in co-ordinated operations across multiple countries.
The targets were organised crime groups which had placed their trust in an encrypted phone application called An0m to arrange drug deals, kidnappings and assassinations.
An informer working for the FBI sold An0m Android phones on the black market, claiming it offered users highly secure encrypted messaging services.
More than 9,000 encrypted devices were in circulation by the time law enforcement agencies pulled the plug on the network on 7 June 2021.
Its users had no idea that An0m had been created by the FBI and that their messages were being collected and analysed by specialists from the Australian Federal Police (AFP) in Canberra and the FBI in San Diego.
Phantom Secure
The FBI operation, codenamed Trojan Shield, has its origins in 2017 when the FBI office in San Diego began investigating the Canadian cryptophone company Phantom Secure.
The investigation revealed that Phantom Secure, run by Vincent Ramos, was supplying secure BlackBerry devices to criminal organisations, offering criminals secure communications that could not be intercepted by law enforcement.
The FBI arrested Ramos in March 2018 in an operation with the Australian Federal Police and the Canadian Mounties.
The take down left a gap in the market for encrypted phones, particularly in Australia where there were an estimated 14,000 users of Phantom Secure involved in drug imports and money laundering.
That gap provided an opportunity for law enforcement. The Australian Federal Police hatched the idea for a follow-up operation with FBI colleagues over drinks.
The idea, said Suzanne Turner, the FBI special agent responsible for the San Diego field office, was to create a new encrypted phone network to compete with others, such as Sky ECC and EncroChat, that were used by criminal groups.
“Realising the marketplace is a small close-knit community, the investigative team came up with an innovative solution to exploit the criminal organisations’ vulnerabilities, which was to create our own closed encrypted platform to offer to the criminal organisations a Trojan horse of sorts,” she told a press conference.
Confidential Human Source
The FBI’s San Diego office recruited a Confidential Human Source (CHS) following the Phantom Secure shutdown to put the operation into action.
The un-named source had previously supplied Phantom Secure phones and another secure phone, Sky ECC, to organised criminal groups.
The CHS had already begun developing “next-generation” encryption technology to compete in the market for cryptophones that become know as An0m or Anom.
The app, modified phones and the An0m platform had been under development for a “considerable time” before law enforcement became involved, said AFP assistant commissioner Nigel Ryan.
The FBI had developed a platform to capture encrypted communications from An0m, but lacked a way of decrypting the messages.
The AFP was able to step in, said Ryan, adding: “We had a very smart individual within the Australian Federal Police who was able to produce some technology that was able to allow us to access, decrypt and read these messages in real time.”
The specialist, working from the living room of his home in Canberra, cracked the problem. He was able to send encrypted messages between two phones and display the unencrypted messages on his laptop in real time.
He filmed a 96-second clip, inadvertently capturing a picture of his bare feet, but it was enough to convince senior officers in the AFP to sign up to a joint investigation with the FBI.
Read more about An0m
- Police in 16 countries carried out raids on after Australian Police and the FBI cracked an encrypted An0m communications network used by crime groups.
- The FBI working with overseas law enforcement has arrested eight people and named a further 13 people accused of distributing An0m phones to organised crime group.
According to Ryan, An0m was the result of “like-minded and passionate individuals in the AFP and FBI thinking differently to solve the common problem of the use of encrypted communications for criminals”.
“Those individuals did conceptualise some of this over a beer. From there, they worked on a plan that could work and was legal,” he said.
The FBI and AFP were able to influence the development of the platform to ensure it remained attractive to the criminal groups.
“The developers did not know who the users of the platform were or that law enforcement agencies were involved in the management of the platform,” said Ryan.
The CHS agreed to offer his technology, known as An0m, to the FBI in return for the possibility of a reduced prison sentence, and received payments of $160,000.
He agreed to distribute An0m phones to his trusted network of distributors who, in turn, provided the phones to organised criminal groups.
By the autumn of 2018, the US Organised Crime Drug Enforcement Taskforce (OCDETF) had identified the operation as a priority operation, providing it with funding and resources.
The FBI’s master key
The CHS, working with the FBI and the AFP technical experts, redesigned An0m to incorporate a “master encryption key” into its software.
Every message was copied to a server outside the US where it was decrypted using the CHS’ master key and re-encrypted with an FBI encryption key. From there, it was passed to an FBI-owned “iBot” server where it was again decrypted and viewed for the first time by FBI officers.
Each phone user was assigned a unique electronic signature, known as a Jabber identification (JID), by the covert human source or another An0m administrator. JIDs were a unique identification code made up of numbers and letters, and on more recent devices consisted of two English words joined together.
An0m users could choose and change their own usernames, but FBI officers were still able to track them through a database that matched their usernames with their Jabber identifications.
The sting
The AFP took on the role of pilot-testing the An0m operation. Its officers had identified distributors which could unwittingly supply compromised phones to crime groups in Australia.
The AFP has been running a covert surveillance programme for 14 years to tackle criminal use of encryption, and has built relationships with industry, developed techniques and tools, and hired technical specialists.
An0m phones offered attractive features for anyone who wanted to communicate securely – the app was hidden on android phones and could only be accessed by typing a secret pin into the phone’s calculator app.

An0m phones were modified so they couldn’t be used in the normal way. They operated in a closed system, allowing users to exchange encrypted messages only with other An0m phone users.
They featured self-deleting messages, but also included features that might be useful to law enforcement.
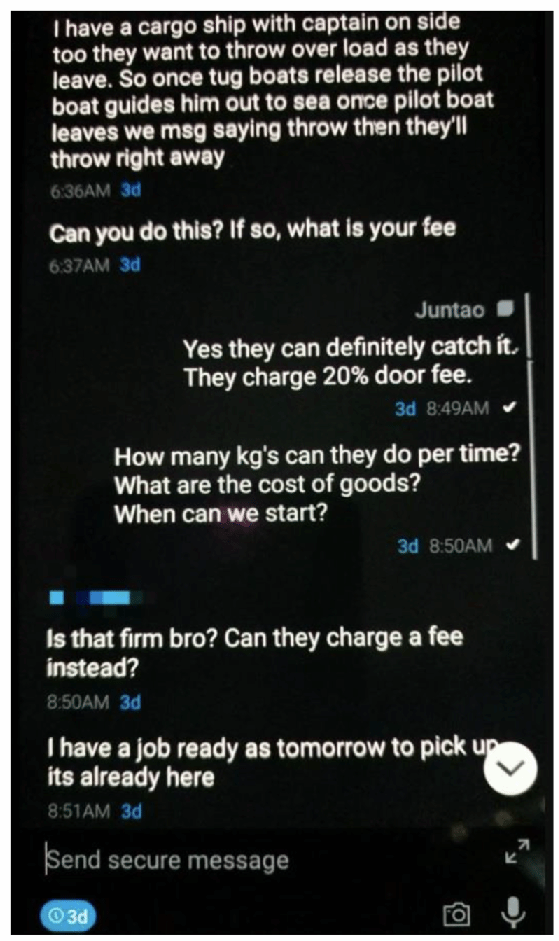
While some encrypted phone networks, such as EncroChat, deliberately disabled the phones camera, An0m phones allowed people to take photos, pixilate them and send photos to other uses. Crime groups, which trusted the phone’s security unquestionably, had no qualms about sharing photographs of their drug hauls, providing investigators with valuable intelligence.
The phones also offered a push-to-talk feature that allowed users to change their voice – another attractive feature for crime gangs.
The target
In October 2018, the FBI’s covert source offered An0m phones to three former Phantom Secure distributors, each with connections to criminal organisations in Australia.
They agreed to take 50 devices to trial in a “beta test”, unaware that the Australian Federal Police had applied court order to monitor the communications of every An0m phone user with a connection to Australia.
One of the targets was “a significant crime figure” in the Middle East, identified as Joseph Hakan Ayik, who police knew could exert a strong influence over the encrypted communications market.
Ayik, an Australia-born 42 year old, was a significant figure in drugs crime and was suspected of heroin trafficking. He was briefly arrested in Cyprus before skipping bail.
An investigation by 60 Minutes Australia, The Age and the Sydney Morning Herald tracked him down in Turkey, where he is alleged to lead a lavish lifestyle.
AFP’s Ryan said: “[Ayik’s] use of the device was perceived as an endorsement, and the platform grew exponentially from there.”
This week, Australian police urged Ayik to hand himself in for his own safety.
The test operation allowed the AFP to penetrate two major criminal networks operating in Australia that used the phones to discuss the shipping of hundreds of kilograms of narcotics and orders for firearms.
Australia’s judicial order to intercept An0m communications did not allow it to share the intercept material with foreign partners, including the FBI.
Investigators from the AFP monitored the messages, and kept the FBI’s San Diego office informed of their progress.
Randy Grossman, acting US attorney general for the Southern District of California, said the criminals had no idea they had fallen into a trap.
“The criminals using these devices believe they were secretly planning crimes far beneath the radar of law enforcement. But, in reality, the criminals were not underneath the radar, they were on it. The FBI was monitoring those conversations,” he said.
The growth of An0m
An0m began spreading slowly in Australia. The phones were sold through word-of-mouth recommendations passed on by a network of criminal distributors set up by the FBI’s informant.
Sales took off during the summer of 2019, as demand increased for An0m phones both inside Australia and from other countries.
According to a US indictment, users in Europe paid a fee of around €1,000 to €1,500 for a six-month subscription. Payments were made in bitcoin and other cryptocurrencies to protect the users’ anonymity and were laundered through shell companies to hide the proceeds.
Specialists at the AFP developed and trained software to identify criminal themes and threats to life in the messages. The software was able to translate communications in foreign languages and to tag the content of images.
“Imminent threats resulted in an automated alert to investigation teams within the AFP and law enforcement partners,” said Ryan.
The investigation team began working with an un-named third country to set up an additional iBot server outside the US to supply intercepted messages to the FBI.
This additional server acted simply as a mailbox sending messages back to the FBI without law enforcement officials in the hosting country reviewing them. By October 2019, the FBI began receiving messages from the iBot from several hundred An0m users largely based in Australia.
Under the agreement, the iBot server delivered updates to the FBI every Monday, Wednesday and Friday, a US search warrant application reveals.
The end of the operation was planned form the beginning. The date,7 June 2021, chosen to conduct co-ordinated raids around the world, was the precise date a court order for the surveillance operation expired.
Under US law, the FBI is not permitted to monitor communications of US citizens, meaning the FBI did not collect messages from devices identified as having US users. Instead, the Australian Federal Police agreed to monitor some 15 devices identified as belonging to US users for messages showing threats to life to US citizens.
Controversial surveillance law
The Australian prime minister, Scott Morrison, confirmed that the country had used its controversial “TOLA law” for the first time to gain access to encrypted communications during the operation.
The Telecommunications and Other Legislation Amendment (Assistance and Access) Act 2018 allows Australia’s law enforcement and intelligence services to order technology companies to assist government agencies in accessing the content of encrypted data.
The government has not given any details on how it used the power in the An0m operation. Morrison declined to say whether Australia’s legal regime was one of reasons the FBI chose to collaborate with Australia.
“Certainly, as a government, we make no apologies for ensuring that our law enforcement authorities have the powers and authorities they need,” he said.
Infiltration of EncroChat and Sky ECC boosts demand
Demand for An0m phones grew after police in France, working with the Netherlands and the UK, announced that they had penetrated another encrypted phone network used by criminals – EncroChat – in July 2020.
In March 2021, French and Belgian police took down a second encrypted phone network, Sky ECC, also claimed to be used by criminal groups, while the FBI issued an arrest warrant for its CEO.
Criminal groups began looking for another safe communications device and many turned to An0m. The number of active users of An0m grew from 3,000 before the closure of Sky ECC to 9,000 by the end of the operation.
Europe joins the sting
The FBI and AFP widened the collaboration to law enforcement operations in other countries as the investigations progressed.
Sweden’s police were among the first in Europe to join the FBI investigation in September 2019 as part of a European operation co-ordinated by Europol.
Europol set up an operational task force to work with the FBI and the AFP in March 2021.
Dutch technical specialists developed technical tools to analyse and interpret millions of messages. The Dutch software was able to map connections between criminal groups, adding to a wealth of data the Dutch had previously gathered from criminals using the EncroChat-encrypted phone network.
The Dutch shared the tools with Europol, which analysed the data and shared the results with other European countries.
Reviewing the data
An FBI team reviewed and translated messages from the iBot server, cataloguing 20 million messages from 11,800 devices.
The phones were used extensively in Germany, the Netherlands, Spain, Austria, and Serbia, but were found in more than 90 countries.
In addition to messages, the FBI intercepted 450,000 images showing discussions on other encrypted platforms, cash, police documents and cryptocurrency transactions.
Each one of the An0m devices intercepted was used for criminal purposes, said the FBI’s special agent Turner. The users are the “upper echelon of command and control” of “transnational criminal organisations and their various international illegal transportation and distribution networks”, she said.
FBI analysts translated and assessed the intercepted messages before sharing them with law enforcement agencies in 40 countries.
Europol’s task force identified 300 organised crime gangs using An0m. They included Italian organised crime groups and motorcycle gangs in Australia.

In one exchange, Australian Domenico Catanzariti, an An0m network administrator, discussed selling 160 boxes of cocaine marked with a distinctive Batman logo for $160,000 AUD a kilogram.
In another case, Baris Tukel, an Australian citizen living in Turkey, offered to sell cocaine hidden inside French diplomatic envelopes from a supplier in Columbia.
Other messages revealed plans by a crime group to ship cocaine, hidden in cans of tuna, from Ecuador to Belgium in a shipping container. The consignment was intercepted by Belgian police, and a second container was seized by police in Ecuador.
Another drugs shipment sent from Costa Rica to Spain was concealed in hollowed-out pineapples. Spanish police were able to intercept the shipment in May 2020, recovering a tonne of cocaine.
The exercise also identified corrupt law enforcement officers who had passed information to organised crime groups. Six law enforcement officers were arrested on 7 June and a dozen investigations into corrupt officers were opened during the course of the investigation.
800 people arrested in raids
On 7 June, when the surveillance warrant expired, 9,000 police across Europe and Australia raided hundreds of premises and arrested more than 800 suspects.
The operation in Europe – codenamed Greenlight – led to the seizure of more than 30 tonnes of drugs, hundreds of firearms, luxury vehicles and $48m in cash and cryptocurrencies.
Sweden’s Polisen searched 100 homes and made 70 arrests. A day later, Spanish police arrested another five Swedish suspects in Spain.
By 8 June, the number of arrests had grown to 155 in Sweden, with further arrests expected to follow.
Dutch police arrested 49 suspects on the first day of the operation, seizing large quantities of drugs, firearms and €2.3m.
In Germany, police arrested 70 people after conducting 150 searches. Many of them were in the Hesse region.

More than 300 police in New Zealand completed 37 search warrants and made 35 arrests, seizing drugs including methamphetamine, firearms, marine vessels and more than $1m in cash.
In Australia, more than 4,000 state and federal police arrested over 200 offenders across the country, in Operation Ironside – shutting down six clandestine drug factories.
The offenders were linked to Australian-based Italian mafia, outlaw motorcycle gangs, and Asian and Albanian crime syndicates.
“We have arrested the alleged kingmakers behind these crimes, prevented mass shootings in suburbs, and frustrated serious and organised crime by seizing their ill-gotten wealth,” said Australian Federal Police commissioner Reece Kershaw.
“Organised crime syndicates target Australia because, sadly, the drug market is so lucrative. Australians are among the world’s biggest drug takers,” he said.
Which network is next?
Kershaw hinted that further police operations against encrypted phone networks may follow.
Despite the take down of An0m, there are even bigger encrypted platforms that are being used by organised criminals targeting Australia, he said.
“They are almost certainly using those encrypted platforms to flood Australia with drugs, guns and undermine our economy by laundering billions of dollars of illicit profit,” he added.
Australian prime minster Morrison used the occasion to press for new surveillance powers, which he said were being delayed because of lack of bipartisan support.
A surveillance legislation amendment would give the AFP and the Australian Criminal Intelligence Commission powers to combat serious crime on the web and to overcome anonymising technology.
“We have law in the Parliament at the moment, which does not have bipartisan support, which we need support for to give them powers to do that,” he said.
Timeline: How the An0m operation unfolded
- 2017: FBI San Diego begins investigating Phantom Secure, which provides encrypted devices to criminal organisations.
- March 2018: A grand jury in the Southern District of California returns an indictment against the CEO of Phantom Secure, Vincent Ramos, and four other principles of the company.
- March 2018 :Vincent Ramos is arrested.
- March 2018: San Diego FBI agents recruit a confidential human source who has been developing the “next-generation” encrypted communications product. The CHS offered the next-generation device, An0m, to the FBI for use in its investigations.
- October 2018: Ramos pleads guilty and was sentenced to nine years in prison and order to forfeit $80m in assets.
- October 2018: The CHS begins offering An0m devices to three former Phantom Secure distributors with connections to criminal organisations, mainly in Australia.
- October 2018: The AFP obtains a court order to legally monitor the An0m devices of people connected to Australia.
- 2019: Growth in the use of devices was initially slow but ramped up by the summer of 2019 inside and outside of Australia.
- Summer 2019: The FBI investigative team engaged representatives from an unidentified third country to receive an iBot server and to obtain communications between An0m users.
- October 2019: The third country obtained a court order permitting it to make a copy of the iBot server and to deliver its contents every two to three days to the FBI.
- 21 October 2019: The FBI begins to receive the server content from the third country. The FBI received data every Monday, Wednesday and Friday.
- July 2020: European investigators announce an investigation into EncroChat. Demand for An0m devices increased.
- March 2021: The US files criminal charges against Jean Francois Eap, CEO of the Sky ECC cryptophone network, leading to a massive increase in demand for An0m devices.
- 12 March 2021: There are close to 9,000 active An0m users.
- 7 June 2021: The third country’s surveillance order expires. Police across Europe, Australia and New Zealand make 800 arrests in a series of co-ordinated raids.









