
GEDIA
Travelex hackers shut down German car parts company Gedia in massive ‘cyber attack’
Car parts manufacturer says cyber attack will have far-reaching consequences for its business, and it has put emergency plans in place to continue deliveries
The criminal group responsible for the cyber attack that has disrupted high-street banks and the foreign currency exchange chain Travelex for more than three weeks has launched what has been described as a “massive cyber attack” on a German automotive parts supplier.
Parts manufacturer Gedia Automotive Group, which employs 4,300 people in seven countries, said today that the attack will have far-reaching consequences for the company, which has been forced to shut down its IT systems and send staff home.
The 100-year-old company, which has its headquarters in Attendorn, said in a statement posted on its website that it would take weeks or months before its systems were fully up and running.
Gedia posted the statement on its website after the criminal group behind the Sodinokibi ransomware attack on Travelex claimed responsibility for the attack on an underground web forum.
“A massive cyber attack was carried out on the headquarters of the Gedia Automotive Group in Attendorn at the beginning of this week,” the company said in the statement. “After discovery and investigation, an immediate system shutdown was decided by the management. This action was taken to prevent a complete breakdown of the IT infrastructure.”
The admission came after the criminal group behind a series of attacks on companies using sophisticated malware that encrypts files, known as Sodinokibi or REvil, threatened to publish sensitive data from the car parts supplier on the internet.
Update – 24 January 2020: Gedia deleted its statement on the hacking attack from its website following publication of this story. The Sodinokibi hacking group has now released further data from Gedia, and issued further threats, in retaliation for what it said were comments made by Gedia’s CEO Markus Schaumburg. Gedia has so far not responded to requests for comment from Computer Weekly.
The group used two Russian-speaking underground forums on the dark web to threaten to publish 50GB of sensitive data, including blueprints and employees’ and clients’ details, unless Gedia agreed to pay a ransom.
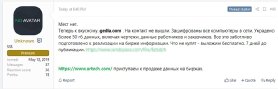
The post read: “Gedia.com. Not contacting us. All machines in the network are encrypted. More than 50GB of data is stolen, including blueprints, employees’ and clients’ details. Everything is thoughtfully prepared to be uploaded to a data exchange platform. What will not be acquired, we’ll share for free. Seven days to publication.”
Gedia said in its statement that the attack had “far-reaching” consequences for the entire group – which has operations in countries including Spain, Poland, Hungary and the US – because all locations are connected to the company’s central IT infrastructure.
“Since large parts of the administration are not able to work due to the shutdown, almost the entire administration employees in Attendorn are initially at home within a flextime rule,” it said.
Emergency plan
The parts manufacturer said it had implemented an emergency plan to ensure production of parts continued, that raw materials were delivered and that it could process customer deliveries.
The company has hired external security experts to analyse the attack and repair the damage. Initial indications are that the attack originated from Eastern Europe.
The group behind the attack, which is thought one of 40 criminal syndicates using Sodinokibi malware, specialises in exploiting known security weaknesses to access companies’ IT systems. It encrypts sensitive data and demands a ransom payment to give companies access to their data.
An individual using the name “UNKN” or “unknown”, posted threats on two Russian-speaking underground hacking forums yesterday threating to sell Gedia’s confidential data and to publish a data that remained unsold on the internet within seven days.
The attackers have released a file containing scans of Gedia’s Microsoft Active Directory, containing details of sensitive user name and passwords, as proof that they have infiltrated the company’s networks.
It reveals that the hackers used a tool, known as ADRecon, that was also used in previous Sodinokibi attacks, to extract data from Gedia.
Computer Weekly has confirmed that the attackers ran the scan on a machine running Microsoft’s Windows Server 2012 software within Gedia’s internal network.
Israeli security company Kela, a specialist in darknet threat intelligence, which identified the ransom message, said the crime groups behind Sodinokibi were using new tactics to step up pressure on companies to pay.
Maya Steiner, threat intelligence team leader at Kela, said: “This is a continuation of the recent ‘attack and brag’ streak of the group. This is the second time they have released ‘proof’ documents, and the first where they announce that they are starting to release full data from a company that has failed to pay.”
The group has also used the Russian-speaking crime forum to step up pressure on another ransomware victim, US computer services company Artech Information Systems, which lists Fortune 500 companies such as AT&T, Mastercard, Bank of America, Capital One and Wells Fargo among its clients.
The hackers published 300MB of data, containing company files stolen from Artech, dating from 2015 to 2019, on the internet on 11 January 2020.
The files are understood to have included the personal mobile phone numbers of company executives, user names and passwords for servers, and instructions for staff on how to connect to remote company servers.
The cyber crime group said yesterday’s post that it would “commence selling data” from Artech.
Artech did not immediately respond to requests from Computer Weekly for comment, however in a previous statement it said that it been hit by a malware attack on 14 January.
“As a precaution, we immediately shut down all of our systems in order to fully investigate the attack and ascertain whether any sensitive or personal data was compromised,” a spokesman said. “While we will continue to conduct further forensic examination, at this stage we believe that no sensitive or personal data has been compromised.”
Unpatched VPN server
According to analysis by US cyber security firm Bad Packets, Artech had an unpatched Pulse Secure VPN server on its network, which left it exposed to ransomware attacks. The company patched the server on 4 January.
Troy Mursch, chief research officer at Bad Packets, said: “Our historical data shows their server was vulnerable from 24 August 2019 until 3 January 2020.”
In practice, the servers would have been vulnerable since late April 2019 when the issue was patched by Pulse Secure, said Mursch.
ADRecon, the security tool used in recent attacks by the criminal groups behind Sodinikobi, was developed by Australian company Sense of Security to allow professionals and ethical hackers to examine the Active Directory on Windows Servers, which is used to control network access and permissions.
Sense of Security’s website says: “Weak passwords, unauthorised user access, outdated/dormant user accounts and weak policies are all common catalysts for security breaches. ADRecon will help organisations identify these shortcomings and address any compliance issues present in the directory.”
Travelex attack
The Sodinokibi hacking group attacked Travelex’s computer systems on New Year’s Eve, forcing the company to turn off its computer systems worldwide.
The attack forced staff at Travelex, which has 1,200 outlets in airports and other retail sites, to use pen and paper to keep track of its sales of foreign currency for three weeks.
The company has been unable to provide online exchange services for its own customers and for high-street banks including Barclays, HSBC, First Direct, Virgin, Clydesdale and Tesco Bank.
The criminal group threated to sell the financial details of Travelex customers in a post on the underground cyber crime forum Exploit on 7 January.
“We recommend that Travelex starts gathering money for payment, or DOB + SSN + CC will be sold to a relevant party,” it said.
The group has made no further comments on Travelex, which has declined to say whether it has paid the $6m ransom demanded by the hackers to decrypt its data.
Travelex said last week that it was making good progress in restoring its operations, but its client banks have yet to restore foreign exchange services.
Additional research by Matt Fowler










