Business priorities: what to protect, monitor and test
How information security professionals can prioritise what to protect, monitor and test in the light of current budget and resource constraints
Information security and IT professionals are being swamped with new challenges that appear to have no easy answers.
Cloud, social networking and bring your own device (BYOD) are obvious concerns, and there are many more equally complex scenarios. Yet budgets and resources are limited.
How do you decide what to focus on? Which systems need additional protection or monitoring? What should we test and how?
The business wants to take advantage of the cost savings and convenience of cloud, the flexibility and productivity of BYOD and the sales and marketing benefits of social networking.
Security staff want to ensure the business is safe from data breaches, secure against attack and compliant with relevant legislation.
If we are not careful, the divide between the business and IT and security will get wider and the organisation will find itself at even greater risk.
All too often, there is also a lack of commitment from senior management. Information security people are told they need to communicate in terms that the board and C-level executives can identify with, yet they are unsure how to do this without losing the critical messages.
There is an approach that will help you identify those areas that urgently need attention, and what the real threats may be and why. As a very attractive by-product, this plan will also help the business understand the risks and encourage them to be part of the solution, not the problem.
Anyone who has worked in security for even a short time will be familiar with threat and risk analysis. Yet how often do information security professionals involve the business in this process, or even follow a formal process at all?
Run a roundtable workshop to identify threats
Here is an alternative that is simple to implement, yet highly effective: by organising a roundtable workshop to identify real threats and real impacts, we can demonstrate the risk and educate our audience in one hit.
You will need a strong facilitator with good security skills to steer the workshop, and representatives from the relevant business departments to participate.
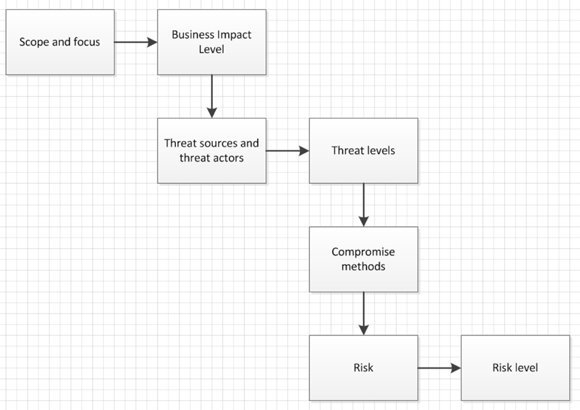
Figure 1 shows the flow of activities for the workshop – this is not rocket science to a security professional. This is your planning tool to make sure the workshop is relevant and produces the desired results. Let’s imagine the business wants to implement a cloud-based HR management system. This is the scope and focus of the workshop.
Next we need to assign the proposed system a business impact level. In this case it will be the human resources representatives, guided by you, who decide how significant an exploit resulting in compromise would be.
Using a simple scale of one to five for each of confidentiality, integrity and availability means that you can give a value to help determine the severity of a potential breach:
- Level 1: Negligible impact
- Level 2: Limited consequences
- Level 3: Significant impact
- Level 4: Very high impact, requiring external assistance and possible financial support
- Level 5: Major risk which seriously endangers business processes and prevents continuity
Threat actors
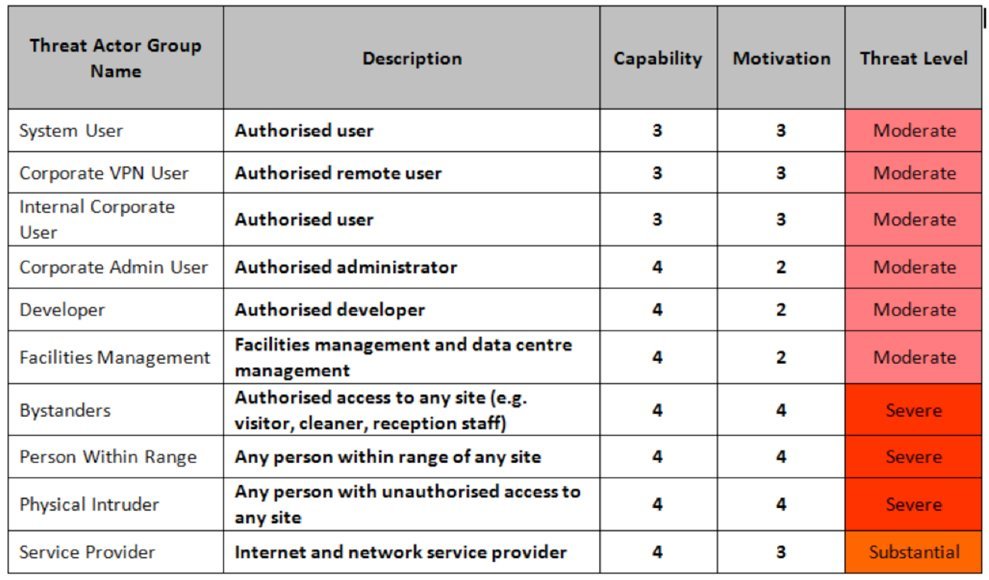
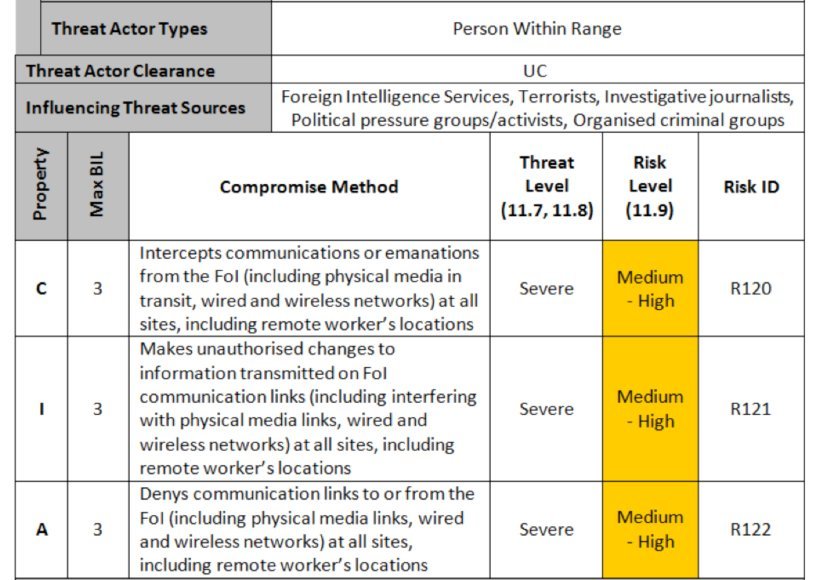
The next stage is to identify "threat actors" for this system (Figure 2). Working from a standard list, you can produce a table of potential threat sources, including users, administrators, service providers, developers, etc.
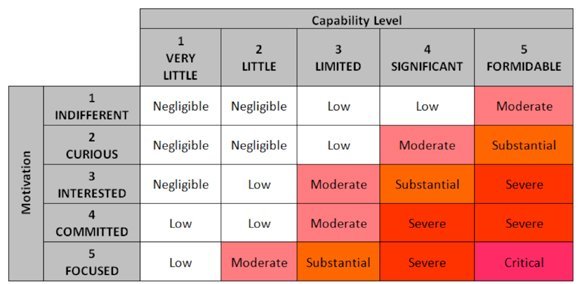
For each actor, assign a capability rating from 1 (very little) to 5 (formidable), and a motivation level from 1 (indifferent) to 5 (focused). This permits you to assign a threat level to each actor, as shown in Figure 3.
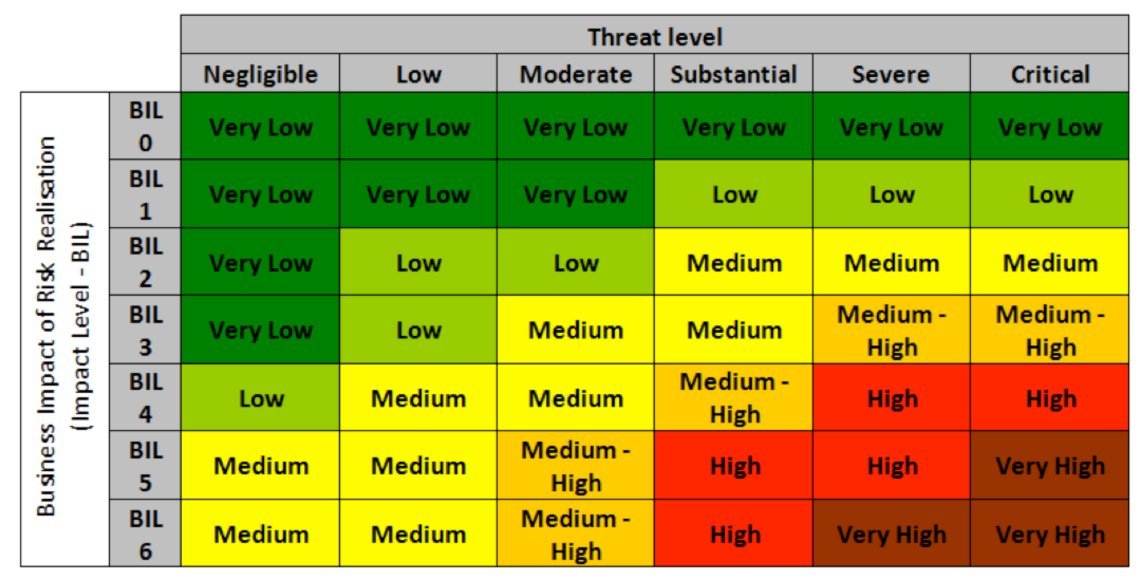
Combine the business impact level with the threat level and you can determine the overall risk for each type of threat (Figure 4).
Now you discuss the types of compromise that each threat actor might attempt which could result in a compromise of confidentiality, integrity and availability and give each a risk ID number. This is the step that needs a strong facilitator to ensure that the group does not spend too long discussing each potential attack.
It is essential that the most common types of compromise are considered and ranked. Figure 5 shows an example for one type of threat actor (note that FoI means focus of interest – in other words, the system under consideration).
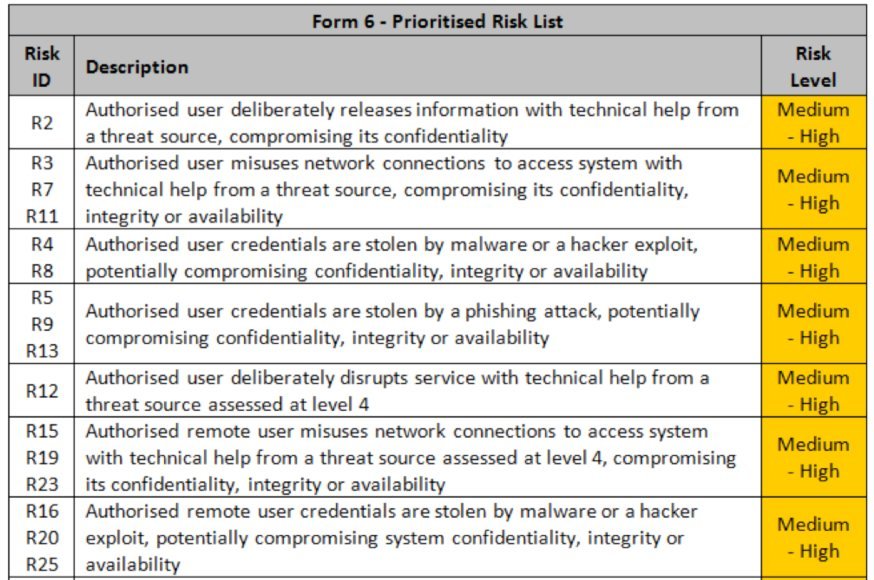
Taking the results of the workshop you can now prioritise the risks for this system and group together similar types of compromise (Figure 6).
Your workshop participants have been part of the journey, helping identify the threats and risks and taking ownership of the potential effects. This means that they will allow you to focus on the most significant threats and even help to decide how to manage them.
This process will identify which threats may need to be simulated in a penetration test and why. It will highlight the systems that require closer monitoring and provide the justification for additional controls where appropriate.
By working through real examples, debating the likelihood of compromises and agreeing the potential consequences to the business, you have created a story which the workshop participants understand and can identify with. You are no longer presenting hypothetical scenarios with little or no resonance to the enterprise.
Once you have run this type of workshop a few times, you will not only find it easier to identify which risks are worthy of your attention, you will also have more business people educated on why security is so important.
The result will be a more risk-aware organisation and much less resistance to the controls and tests that we know are so critical to keep the business safe.
Peter Wood is chief executive officer of First Base Technologies LLP
Image: iStockphoto/Thinkstock