Trousseau turns up truss torque for Kubernetes
Protecting access to sensitive data in Kubernetes is complicated.
Some would go far enough to say that the security layer in Kubernetes is not optimal.
Named after the French for ‘truss’ or ‘turn up’, the Trousseau open source project software aims to lock down an important element of security by enabling secrets management, which can now be added to Kubernetes along with support for any key management encryption, starting with HashiCorp Vault.
Trousseau open source software is available here on GitHub.
Romuald Vandepoel, principal cloud architect with Ondat and the project lead for Trousseau has said that secrets management has always been one of the most difficult issues in Kubernetes and Trousseau Vault integration provides the long-sought answer to that problem.
As BeyondTrust reminds us, “[In software] secrets management refers to the tools and methods for managing digital authentication credentials (secrets), including passwords, keys, APIs and tokens for use in applications, services, privileged accounts and other sensitive parts of the IT ecosystem.”
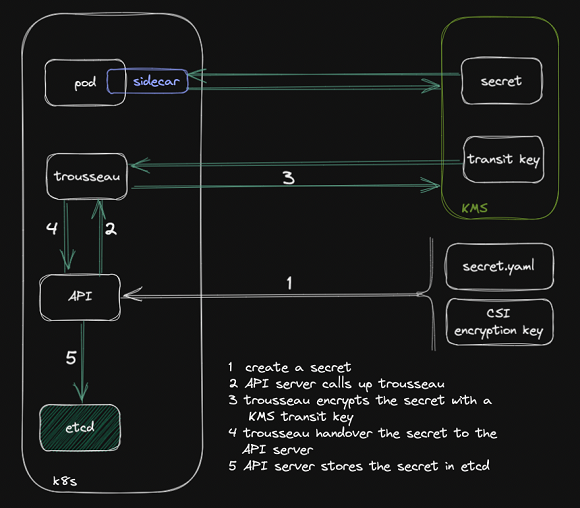
Trousseau uses Kubernetes etcd to store API object definitions and states.
The Kubernetes secrets are shipped into the etcd key-value store database using an in-flight envelope encryption scheme with a remote transit key saved in a KMS.
Kubernetes API primitives
Secrets protected and encrypted with Trousseau and its native Kubernetes integration can connect with a key management system to secure database credentials, a configuration file or TLS (Transport Layer Security) certificate that contains critical information and is easily accessible by an application using the standard Kubernetes API primitives.
“We’re realising two big benefits of Trousseau – first, simplicity as a plugin with the existing KMS, HashiCorp Vault and second, integrating with GitOps workflows using the native Kubernetes API,” said Bill Wong, CEO, SunnyVision Limited. “It’s provided us with the added security we need without disruption.”
With Trousseau, any user/workload can leverage the native Kubernetes way to store and access secrets in a safe way by plugging into any KMS provider, like Hashicorp Vault (Community and Enterprise editions), using the Kubernetes KMS provider framework.
No additional changes or new skills are required.
It’s also possible to transition among Kubernetes platforms using the consistent Kubernetes API.
Trousseau is currently being rolled out in a production customer implementation on Suse Rancher Kubernetes Engine 2 leveraging Ondat as the data management platform, along with Hashicorp Vault.
For more information, read How to keep a secret secret within Kubernetes.