Slicing open The Onion Router (Tor) with no tears
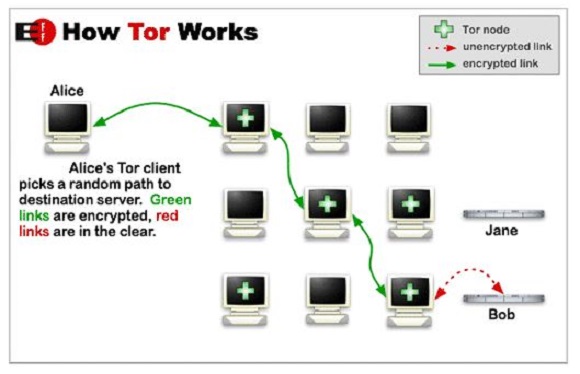
Tor is free and open-source software for enabling anonymous communication by directing Internet traffic through a free, worldwide, volunteer overlay network consisting of more than seven thousand relay servers in order to conceal a user’s location and usage from anyone conducting network surveillance or traffic analysis.
Tor used to stand for The Onion Router; however, this acronym has since been removed in favour of a simple name of the same spelling (Tor).
The Onion Router is a reference to the several layers of encryption wrapped around a user’s internet traffic.
The dark web is of course a reference to websites/services that use the Internet but require specific software, configurations, or authorisation to access them. Tor is the largest of these services/private networks.
These restricted websites hosted on Tor use to be called Hidden Services but are now called Onion Services.
Websites hosted as Onion Services are anonymous, so their location cannot be tracked. As a result, Onion Services are often used to sell stolen credit card information, sell drugs/illegal paraphernalia, or are used by whistle-blowers to publish stolen information or communicate with journalists.
Some examples of Onion Services hosting illegal content include the Silk Road, Agora, and the Tor Carding Forum.
To access these sites, one simply needs to download Tor, open the Tor browser and enter the domain name (.onion domain – similar to .com). Due to these restrictions, the dark web is not indexed by web search engines/content change and detection services like Google/Google Alerts.
AlerTor
AlerTor was created by Luke Millanta, a Sydney-based software developer, esports entrepreneur, and the current chief technology officer at Hive Gaming.
Millanta explains how this technology works and writes as follows from this point forward…
The system I have developed, AlterTor, allows for the indexing of Onion Services and may assist in tracking illegal activity across the Tor network.
AlerTor is an open source content change detection and notification service that has been developed to specifically monitor Tor-based Onion Services (the dark web) for particular keywords.
AlerTor can be used in a number of different ways:
-
To be alerted when your company is being mentioned on dark web forums or message boards.
-
To track user activity across one or multiple forums or message boards.
-
To detect illegal activity (sales of drugs, stolen credit cards etc.).
-
To monitor extremist forums for information relating to protests (both the pre-planning and the aftermath – where people often brag about what they have done).
How does it work?
There are three main components to AlerTor:
-
A database for storing both the user inputs (alert strings) and a list of Onion Services.
-
A data cache for storing text-only (individual page source code) caches of Onion Services.
-
A Python service that:Is able to crawl and cache Onion Services listed in the database. It can also append newly discovered Onion Services to the database (if website1.onion links to website2.onion, the service checks to see if website2.onion is present in the database table. If it is not, it will be added and subsequently cached). Plus it can also scan newly cached/updated pages for alert strings… and notify (by email) users to the presence of any alert strings.
So How many sites does AlerTor have access to? AlerTor is able to access and scan an infinite number of websites, just like any web crawler or content change detection service.
At the moment, however, due to the service still being in somewhat of an MVP stage, the service has only had a small period of time to grow. At the moment AlerTor monitors just over 200 Onion Services, approximately half of which are engaged in some sort of criminal activity (drug marketplaces/carder message boards etc).