Cilium speeds sidecar-optioned cloud-native networking
The Cilium project has reached general availability of Cilium 1.12.
Great news, they’re (the Cilium team) excited… and so are we, but what is Cilium?
Cilium is widely regarded as a (if not the) de-facto standard for cloud-native networking and security… it is open source software designed to handle the tasks associated with providing, securing and observing network connectivity between container workloads in cloud-native worlds.
Major features in the 1.12 release of Cilium have been contributed by Datadog, F5, Form3, Isovalent, Microsoft, Seznam.cz, The New York Times and others.
Entomology fans will be happy to be reminded of the fact that Cilium takes its name from cilium, plural cilia (from Latin ‘eyelash’) a membrane-bound organelle (specialised structures that perform various jobs inside cells) found on most types of cells and certain microorganisms known as ciliates.
What better name could there be for cloud-native neural network interlacing than one taken from nature denoting a membrane-bound organelle?
Answer: there isn’t.
Sidecar software selection
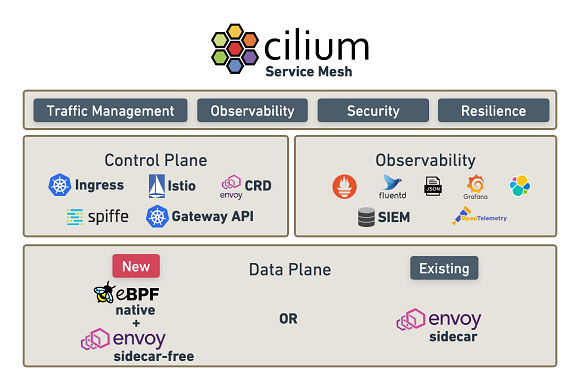
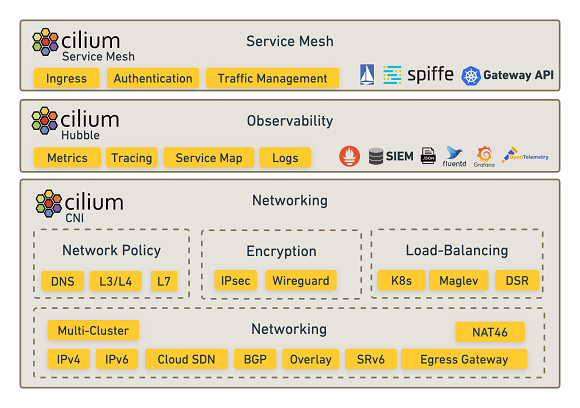
With the release, Cilium has introduced Cilium Service Mesh, a new open source entrant into the service mesh category and one that is claimed to be the first service mesh that gives enterprises the flexibility to run service mesh in a sidecar model or a sidecar-less model and with a broad choice of different control planes.
Did you say sidecar [software] model? Yes, we did… so what does that mean?
Just as a motorcycle sidecar is decoupled from its ‘parent engine’ (the bike), in a sidecar software model, selected application functionalities are segregated from the core application codebase to run concurrently, sequentially or perhaps intermittently. This loosely coupled design pattern approach opens the door to using additional third-party application components without necessarily having to configure them with code that would be required were they part of the parent application.
In addition, this release has also introduced a fully compliant Kubernetes Ingress controller directly integrated into Cilium.
The vision for Cilium Service Mesh is a service mesh built using native Kubernetes resources, just like Cilium’s ClusterMesh uses Kubernetes Services and NetworkPolicy to perform multi-cluster connectivity.
“Cilium Service Mesh is all about choice,” said Thomas Graf, Cilium creator and Isovalent CTO and co-founder. “Enterprises want the ability to choose sidecars or sidecar-less… and they want a high-performance data plane powered by eBPF and Envoy that allows them to choose the best control plane for their use case. By combining the well proven Envoy proxy with kernel-level eBPF technology, Cilium Service Mesh is giving enterprises the best possible service mesh performance, while also allowing them to choose between a sidecar or sidecar-less model.”
With the release, Cilium Service Mesh also introduced CiliumEnvoyConfig (CEC), its low level abstraction for programming Envoy proxies directly with a new Kubernetes Custom Resource (CRD) for advanced L7 use cases to make the full feature set of Envoy available to all users.
Other Cilium 1.12 features
Besides the new sidecar-free Service Mesh option, Cilium 1.12 also features a fully compliant Kubernetes Ingress controller directly embedded in Cilium. It’s powered by Envoy with eBPF used to secure it and provide visibility around it.
In Cilium 1.12, ClusterMesh can treat services running on multiple clusters as a single global service with affinity taken into account. With service affinity, services can be configured to prefer endpoints in the local or remote cluster, if endpoints in multiple clusters are available.
Egress Gateway, previously introduced as a beta feature, is now stable. Cilium allows you to forward connections to external, legacy workloads through specific Gateway nodes, masquerading them with predictable IP addresses to allow integration with legacy firewalls that require static IP addresses. When combined with ClusterMesh, external workloads can support requests that ingress on other clusters in the mesh.
Over the next releases, Cilium Service Mesh will add support for additional service mesh control planes, starting with the Gateway API and its GAMMA initiative for Service Mesh use cases. This will make the Cilium Service Mesh data plane compatible with the service meshes such as Istio which are already migrating to Gateway API.