Splunk expands SOAR security tools amidst 'oceans of data'
Splunk has expanded its cyber threat security portfolio with advanced software-as-a-platform powered Security Automation, Orchestration and Response (SOAR) features.
Here we find a use case library and event sequencing technologies now being shipped in Splunk Security, a package that promises what Splunk has called ‘machine-speed response’.
“As security threats increase in both velocity and complexity, our customers have a more urgent need to take action on their data so they can respond to vulnerabilities at machine speed,” said Haiyan Song, senior vice president and general manager of security markets, Splunk.
This is a combination of Splunk ES, Splunk UBA and (the more recently acquired) Splunk Phantom.
Oceans of data
Splunk says the global economy continues to rapidly digitise and in so doing it creates ‘oceans’ of security-relevant data and ever-growing digital footprints. In parallel, a rising volume of cyber criminals executing increasingly sophisticated, automated attacks are challenging Security Operation Centers (SOCs) to keep up with the new attack surface, which lives on premise and in the cloud.
Splunk insists that its security solutions allow customers to see the entire threat, versus an individual incident.
The firm’s expanded suite of security solutions is said to help security analysts monitor, visualise, detect, investigate and act on internal and external threats via Splunk’s security information and events management (SIEM) platform.
Following Splunk’s acquisition of Phantom earlier this year, customers can now also take action on their data via Phantom’s security SOAR technology.
Threat event sequencing
Splunk unveiled a range of new features to its flagship SIEM platform, including new event sequencing, which groups correlation searches and risk modifiers to optimise threat detection and accelerate investigations – also here is a new use case library, which gives Splunk ES customers ready-to-use, research-driven and actionable security content that is relevant to their security operations.
The branded Splunk ES Use Case Library gives customers an automatic way to discover new use cases, such as adversary tactics, cloud security, abuse or ransomware, to determine how to take action on threats within their own environment.
“To build resiliency, organisations are recognising that they need an analytics-driven security platform that merges security information and event management (SIEM) and user behavior analytics (UBA) functionality,” said Robert Boyce, managing director, Accenture Security.
Splunk Phantom’s SOAR technology aids SOCs to orchestrate tasks and automate complex workflows.
The company says that with Splunk Phantom 4.0, customers gain access to a range of new features, including clustering support, which helps customers scale their operations; a new indicator view, which gives analysts a threat-intelligence-centered way to perform investigations and improved onboarding, which enables customers to take action with Splunk Phantom ‘within minutes’ of deployment.
Anomalous user behaviour
New features in Splunk UBA 4.2 include user feedback learning, which enhances Splunk UBA anomaly model scoring to improve severity and confidence in threat detection; improved data ingestion performance by up to 2x, which strengthens data quality; and new single-sign-on authentication support, which helps SOC teams maintain compliant access controls across their security nerve centre.
Splunk also announced the launch of the Splunk Adaptive Operations Framework (AOF).
An evolution of the Splunk Adaptive Response Initiative, enhanced with the flexible API-driven framework from Splunk Phantom, Splunk AOF is a community of industry security vendors.
“With Splunk AOF, organisations can use Splunk in tandem with over 240 security technologies to ingest structured or unstructured data from any source, drive coordinated decisions supported by analytics and take action across a comprehensive range of technologies in the SOC,” noted the firm, in a press statement.
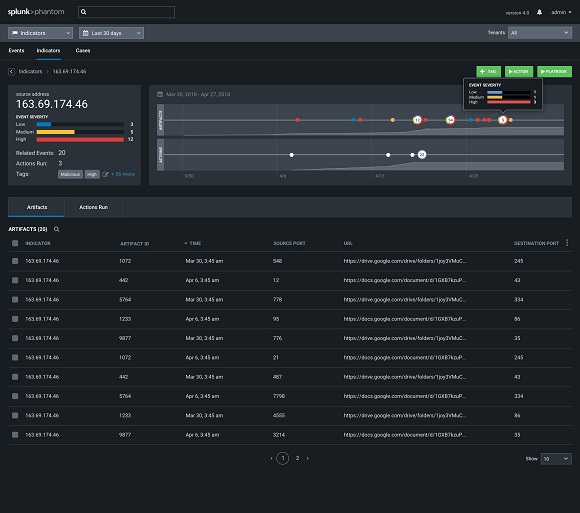
Splunk Phantom 4.0 provides ‘threat hunters’ with indicator-centric visualisations of security data.




