Top European IT initiative to support business in 2014?
Expanding IT to support business growth is one of the biggest areas of focus for IT departments in 2014, so what does this mean?
Expanding IT to support business growth is one of the biggest areas of focus for IT departments in 2014, so what does this mean in terms of activity and investment?
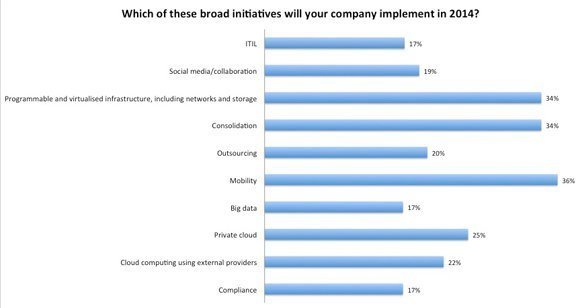
This will include IT consolidation, virtualisation and cloud computing, but topping the list of intiatives for 2014 is mobility, according to the annual IT priorities survey by TechTarget and Computer Weekly (see chart below).
This is not surprising. Yahoo's chief executive, Marissa Mayer, recently declared at the Consumer Electronics Show (CES) in Las Vegas that: “We are in the midst of a massive and continuing platform shift to mobile.”
According to the research, 36% of IT departments in Europe and 37% in the UK intend to implement broad mobility initiatives in 2014, with 67% planning to give employees more mobile devices.
Unsurprisingly, then, smartphones and mobility feature among the top five highest profile projects for the coming year, closely followed by mobile applications.
In Europe and the UK, mobile has moved up from seventh position in 2013 to fifth in 2014 in the ranking of deployment models that companies plan to use in the year ahead, displacing public cloud and platform-as-a-service.
However, with several high-profile customer data breaches in recent months, it appears that businesses are finally recognising the importance of data security.
“Data leakage is a killer for businesses and CEOs know it. Every organisation must have technical safeguards and formal HR/IT policies in place that protect business information,” said Phil Barnett, UK sales director for Good Technology.
“The spectre of fines and/or reputational damage can cause organisations to go in to lock-down, but this will severely damage the transformational capability that mobility brings. Therefore CIO’s need to deliver top-grade security, without compromising user productivity,” he said.
This is particularly important when many security researchers expect consumers and businesses to feel the impact of mobile malware in 2014.
“I suspect that in 2014 we will see mobile malware reach new levels of sophistication as BYOD becomes more prevalent in the workplace,” said Craig Young, researcher at Tripwire Security.
“Mobile devices may be targeted not only for the data they store but also for the systems and services they can access,” he said.
More on BYOD
- BYOD: data protection and information security issues
- Government approves BYOD for public sector staff
- More than one billion BYOD users predicted by 2018
- CW500 Club: BYOD best practice
To combat this threat, Young said users need to become more vigilant about the applications they install and the networks they connect to with their smartphone or tablet.
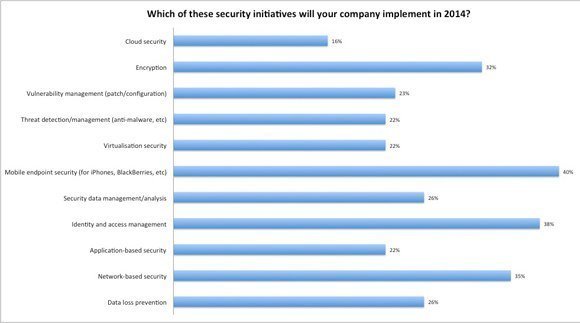
From the research by TechTarget and Computer Weekly, it is reassuring to see that 32% of respondents plan mobile endpoint security projects, 30% plan mobile device management projects and 26% said they plan mobile security projects.
More specifically, 31% of respondents said their companies plan to implement security initiatives for mobile devices.
The same proportion plan data loss prevention and identity and access management initiatives, while 35% said they plan network-based security initiatives.
Underlining the growing emphasis on mobile security is that fact that fewer initiatives are planned in threat detection (27%), vulnerability management (26%), virtualisation security (24%).
Mobile security even tops the proportion of European companies planning intiatives in encryption (24%) security data analysis (23%), cloud security (21%) and application-based security (20%).
In the UK, however, mobile security tops the list of priorities, moving up from sixth position in 2013, with 40% of companies polled indicating they plan initiatives in this area in the coming year.
Mobile security is also among the top five mobility initiatives that companies plan to implement in 2014, accounting for an average of 22% of mobility projects across Europe and 30% in the UK.
And finally, underlying the emphasis on security for mobile devices, most companies plan to purchase smartphones for employees (44%).
Fewer companies plan a combination of corporate purchase and individual choice, and despite the apparent rise of BYOD policies, just 17% said they will allow employees their own choice.
While educing users on security is widely acknowledged as a vital part of ensuring mobile security, the technical controls remain important.
This is particularly true when it comes to requirements by data protection legislation for wiping or immobilising lost and stolen devices.
However, Good Technology believes that although the principle is sound, a brute force approach opens up a range of privacy issues.
“Even if employees are made to sign wiping agreements, it is feasible that the destruction of personal data could result in civil cases,” said the firm’s Phil Barnett.
“If companies ensure data is held in secure containers on devices, the need for entire-device wiping does not arise.
More on security
- Cyber Security Summit 2014
- Security Think Tank: Snowden likely to prompt security reviews
- Security considerations for UK enterprises
“Limiting access to a secure container means the container can be revoked without destroying anything else stored on the device,” he said.
Barnett believes that in 2014, organisations the world over will increasingly challenge their IT teams to move towards a secure user-led BYOD policy.
The result, he said, is that more organisations will be re-assessing secure mobility, and the decisions they make will affect their company for the next ten years, underlining the importance of mobile security projects in the coming year.
Download your copy of IT Priorities Europe 2014
Benchmark your IT spending plans with our in-depth study of IT spending priorities in the UK, France, Germany, and Europe in 2014.
But Ovum analyst Andrew Kellett points out that not every organisation has the budget or security resources to meet its current protection requirements, let alone the BYOD-driven use of smartphones and tablets.
“Therefore, organisations will be forced to consider the practicalities of managed, security-as-a-service options,” he said.
Looking forward, RSA executive chairman Art Coviello predicts that the next evolution of the BYOD trend will be the consumerisation of identity as employees increasingly push for a simpler, more integrated system of identification for all of the ways they use their devices.
“Identity will be less entrusted to third parties and increasingly be something closely held and managed by individuals – as closely as they hold their own devices,” he said. According to Coviello, 2014 will be the dawn of Bring (and control) Your Own Identity (BYOI).
With increased attention on mobile computing to support the business, it will be interesting to see through the coming year, just how that translates into action, particularly regarding security in the next 12 months.










